Prerequisites
- Active Qovery application
- Domain ownership on Cloudflare or registrar
- Access to Cloudflare DNS settings
Step 1: Add a Custom Domain
- Access your application settings in Qovery Console
- Navigate to the Domains section
- Enter your Cloudflare-managed domain
- Critical: Enable the “Domain behind a CDN” toggle
Enabling “Domain behind a CDN” automatically disables certificate generation since Cloudflare handles SSL/TLS management.
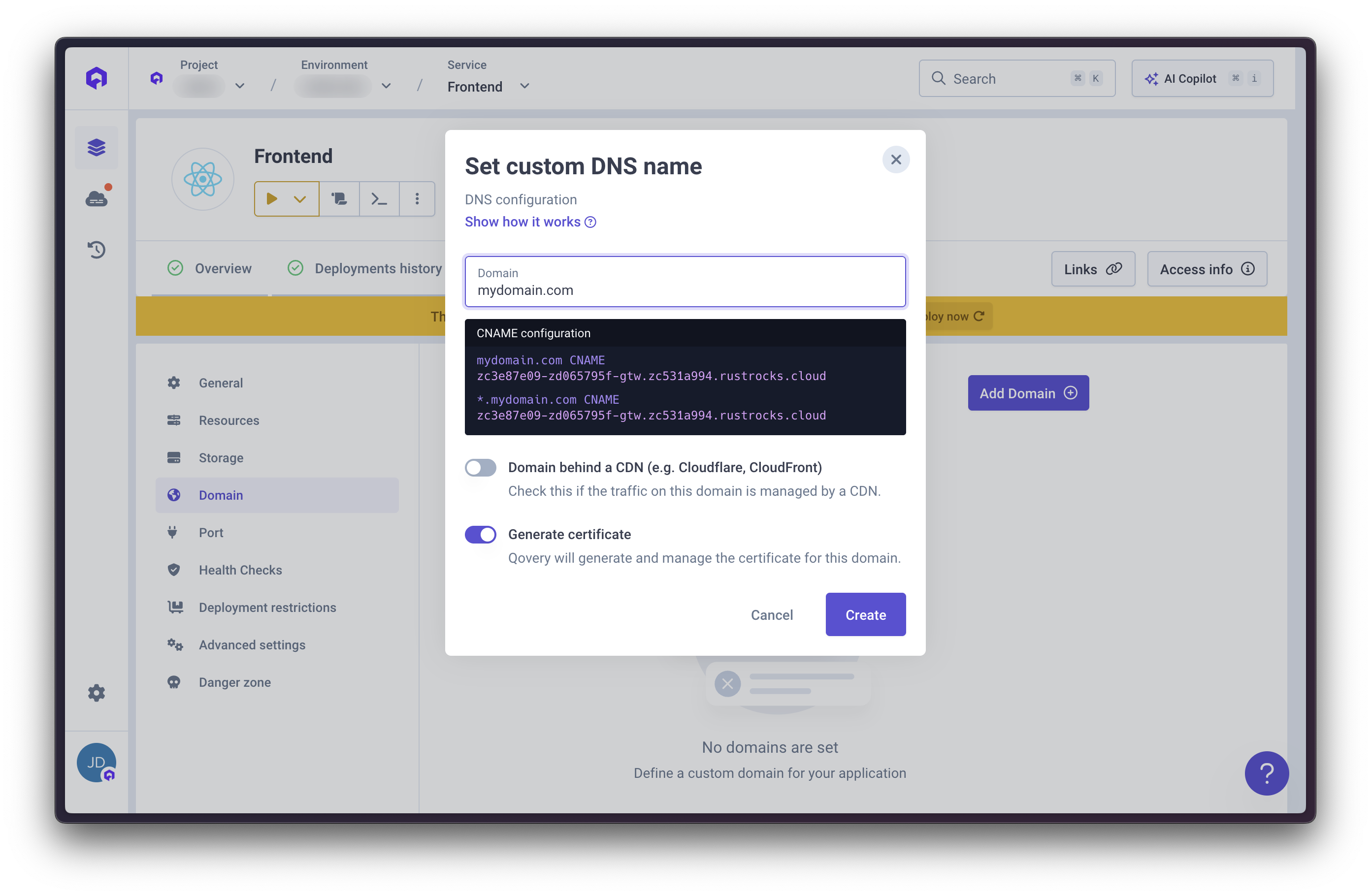
Step 2: Configure Cloudflare DNS
Add CNAME Entry
- Go to Cloudflare DNS settings
- Add a CNAME entry using values provided by the Qovery Console
- The proxy mode can remain enabled
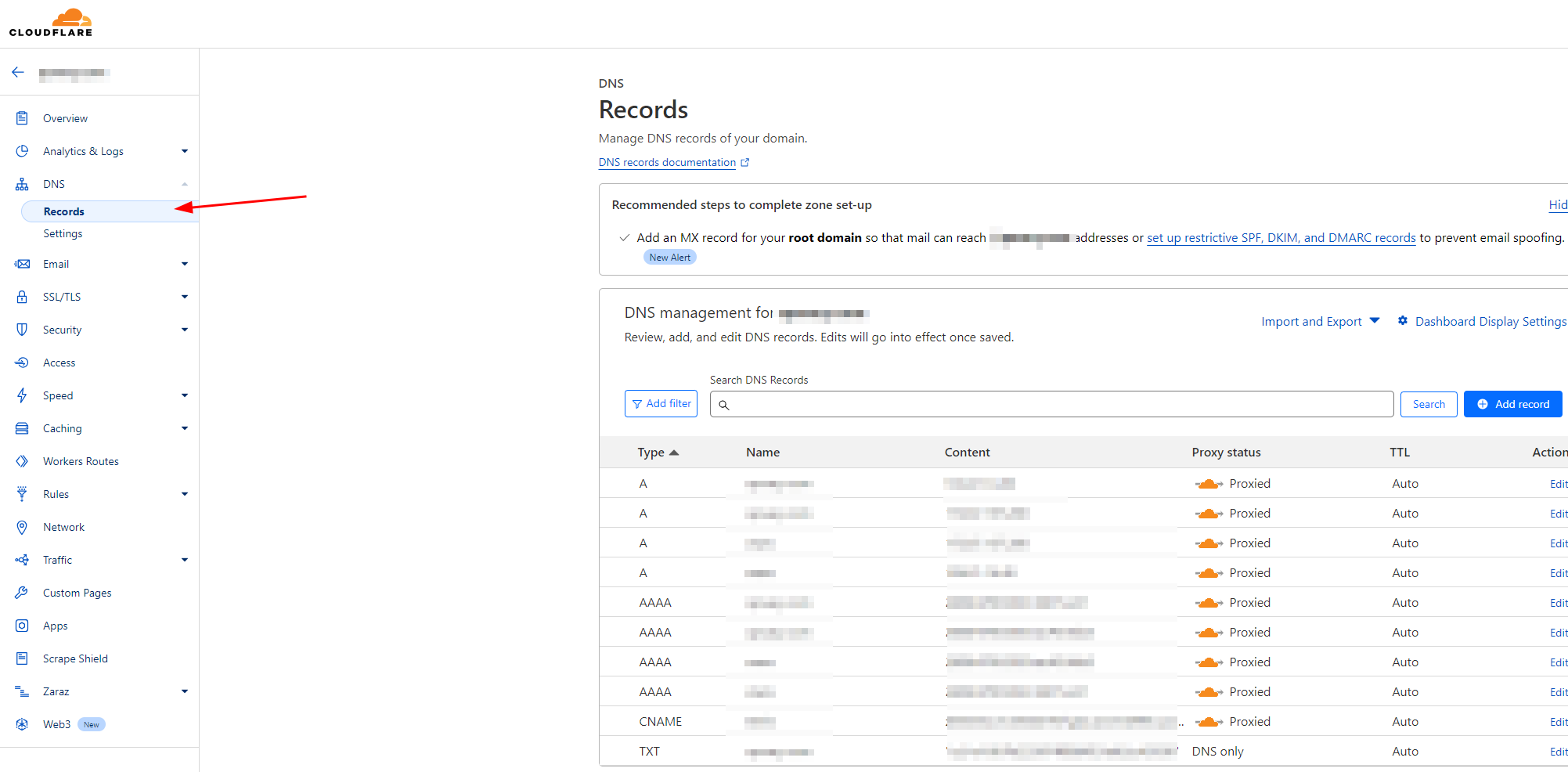
Step 3: Configure SSL/TLS Settings
The last step to configure the domain Cloudflare side properly is to use the Full TLS encryption for proper custom domain functionality.- Navigate to SSL/TLS settings in Cloudflare
- Select Full encryption mode
Step 4: Access Restriction Options
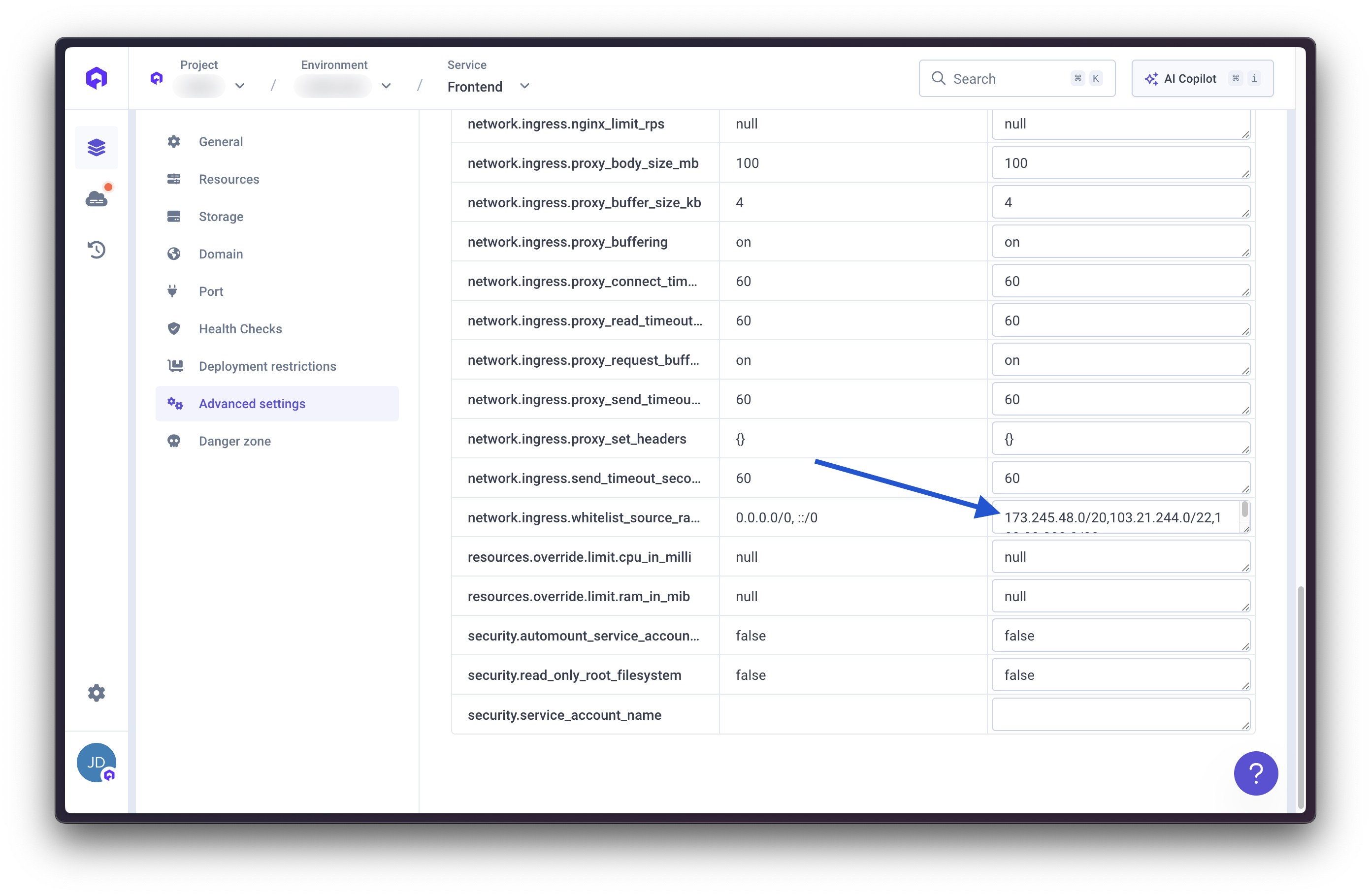
You have two options for restricting access to your application:Option 1: IP Whitelisting
Add Cloudflare IP ranges to Qovery’s advanced settings to allow only Cloudflare traffic.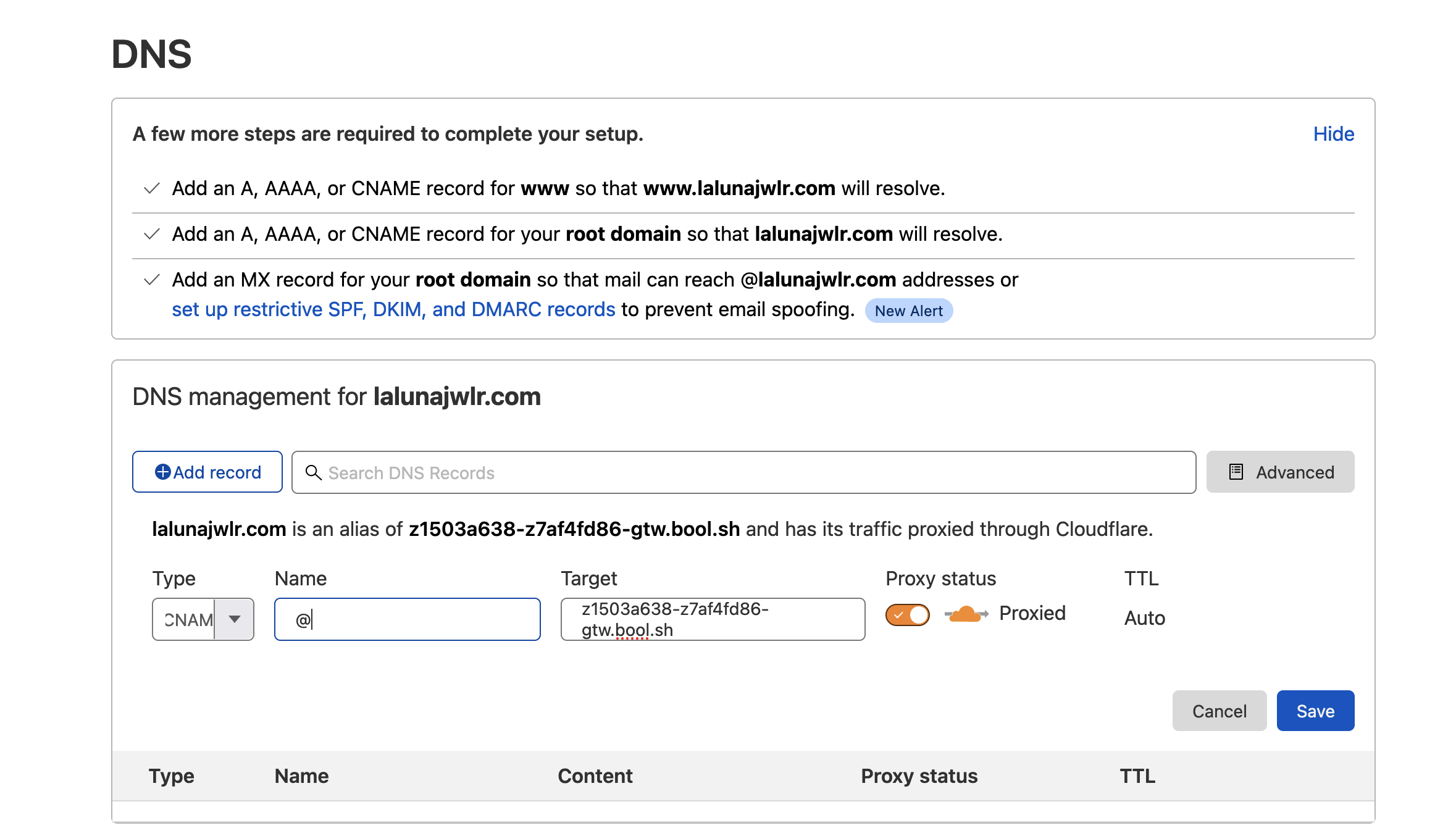
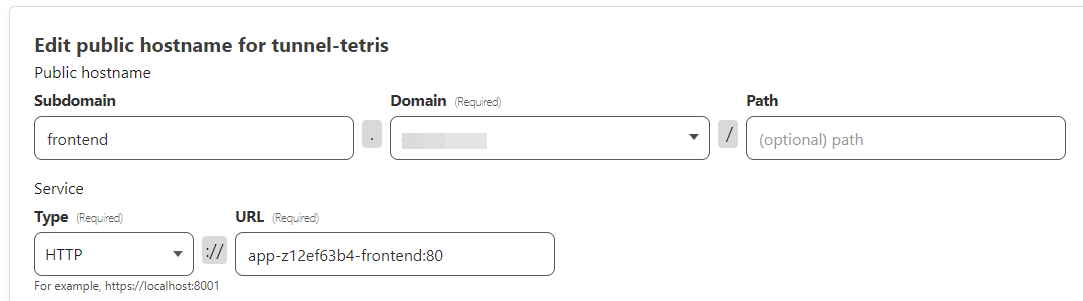
Option 2: Cloudflared Tunnel
Cloudflared establishes outbound tunnels between resources and Cloudflare’s network, enabling tunnel-based access without public exposure.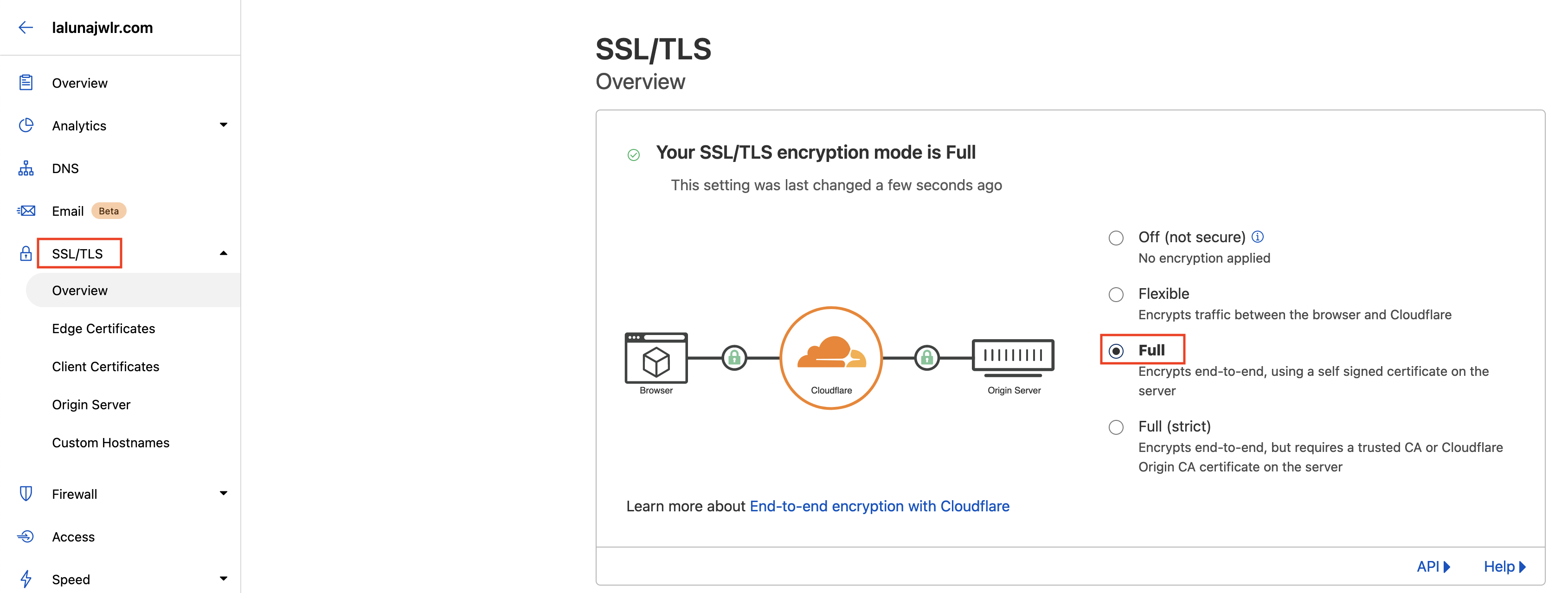
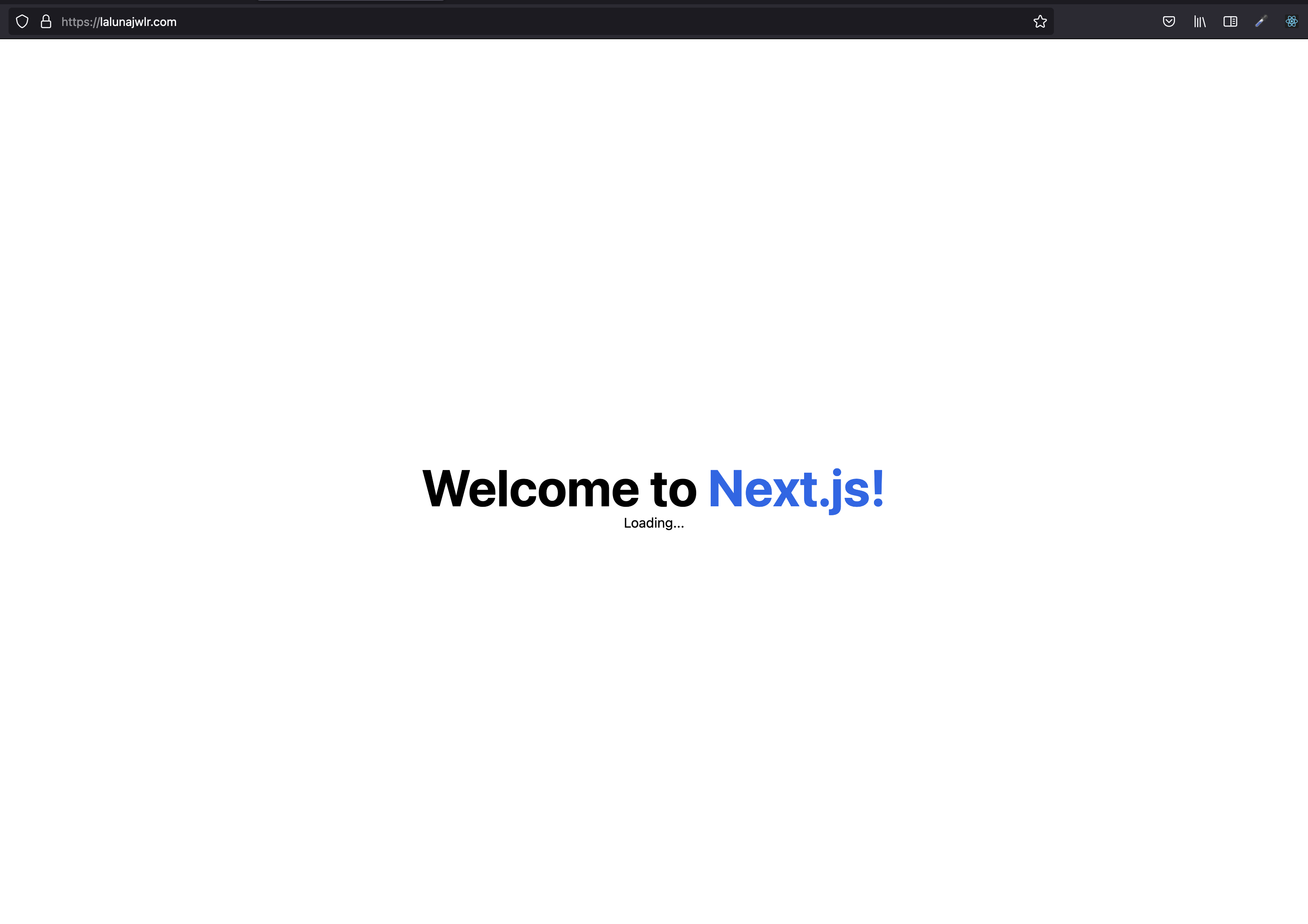
Verification
Once configured, your application should be accessible via your custom domain through Cloudflare’s network.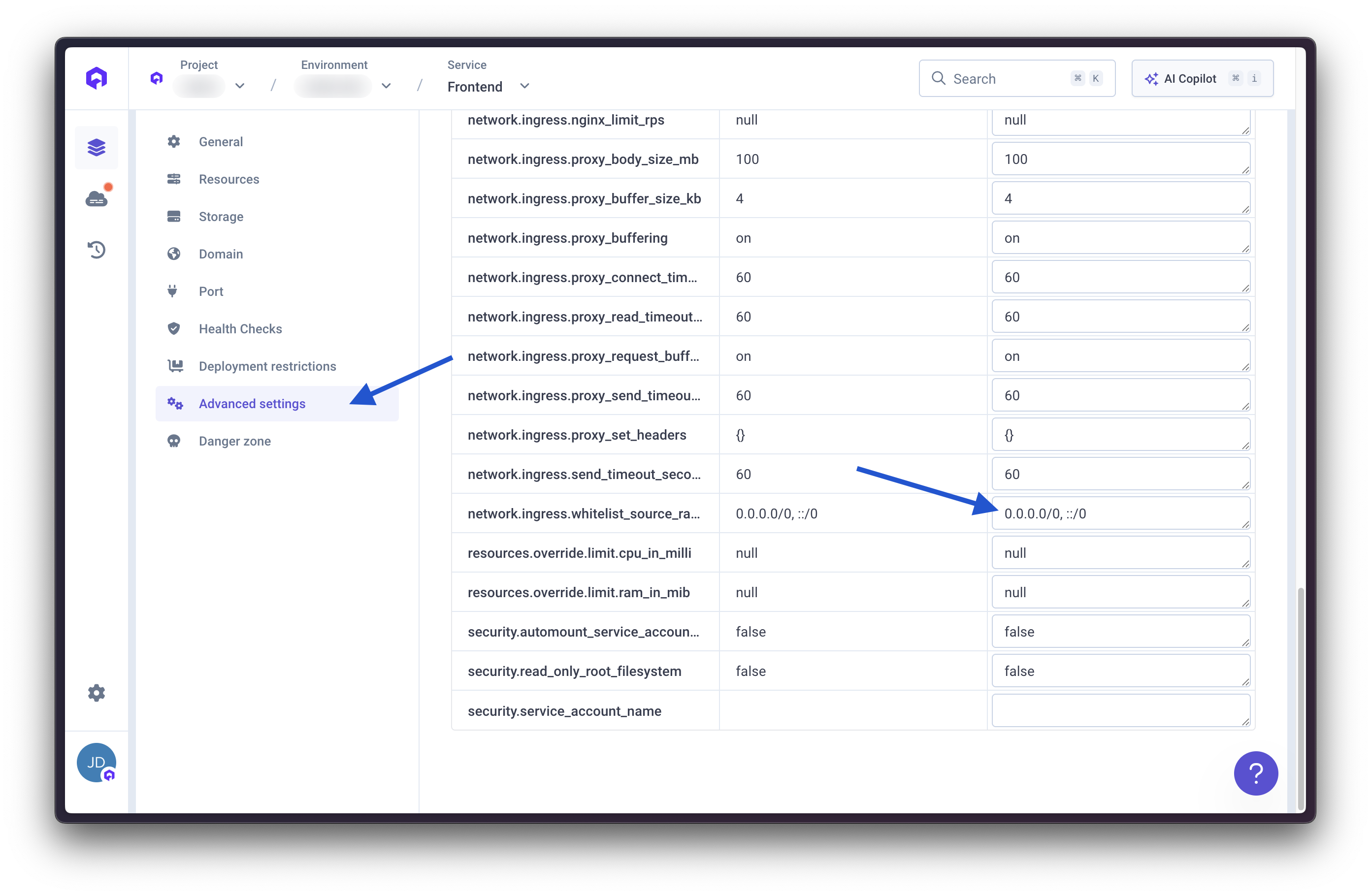
Additional Configuration
Advanced Cloudflare Features
You can leverage Cloudflare’s additional features: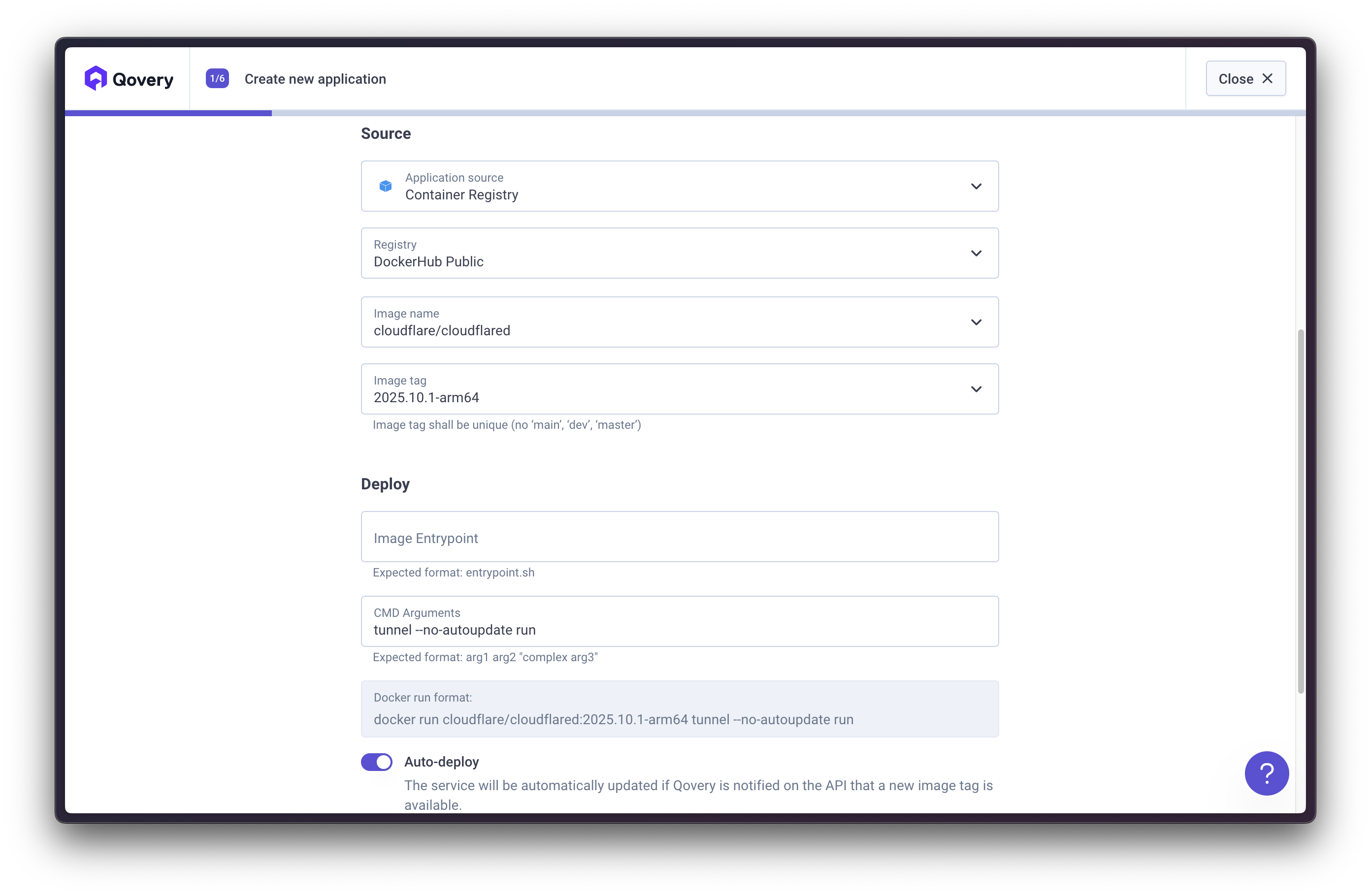
Troubleshooting
Domain not resolving
Domain not resolving
- Verify CNAME record is correct
- Check DNS propagation (can take up to 48 hours)
- Ensure proxy mode is enabled in Cloudflare
SSL/TLS errors
SSL/TLS errors
- Confirm “Full” encryption mode is selected
- Wait for SSL certificate provisioning (5-10 minutes)
- Check that “Domain behind a CDN” toggle is enabled in Qovery
502 Bad Gateway errors
502 Bad Gateway errors
- Verify application is running in Qovery
- Check that the CNAME points to the correct Qovery domain
- Ensure Cloudflare IP ranges are whitelisted if using IP restriction

