Goal
Establish these business requirements:- Incoming requests must include custom HTTP header
X-QOVERY-SOURCEwith values: staging, production, or development - IP ranges mapped to each source:
- Staging:
10.42.0.0/16,10.43.0.0/16 - Production:
10.44.0.0/16 - Development:
92.xxx.xx.171
- Staging:
- Requests from unauthorized IP ranges for their source are rejected
- Requests lacking the
X-QOVERY-SOURCEheader are rejected
Initial Setup
Cluster Configuration
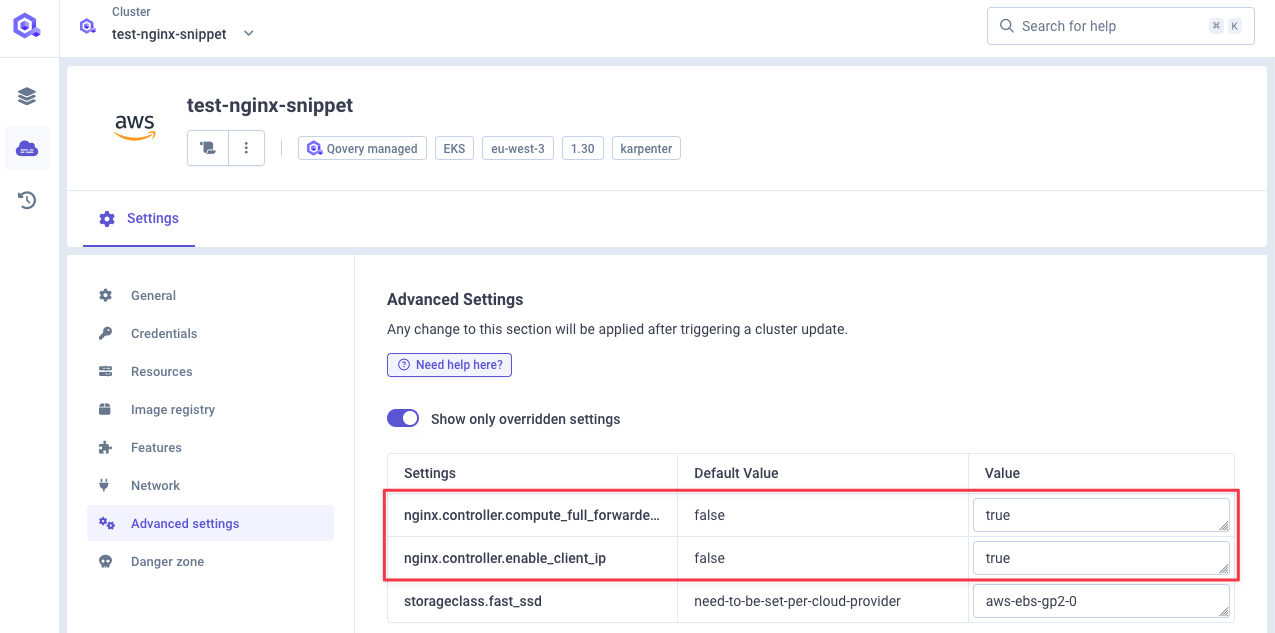
- Go to Cluster Settings → Advanced Settings
- Enable
nginx.controller.enable_client_ip - Enable
nginx.controller.compute_full_forwarded_for
Deploy Test Service
Use echo-server container listening on port 80 for testing.Configuring Authorization
Step 1: HTTP Snippet Declaration
Configurenginx.controller.http_snippet with geo and map directives:
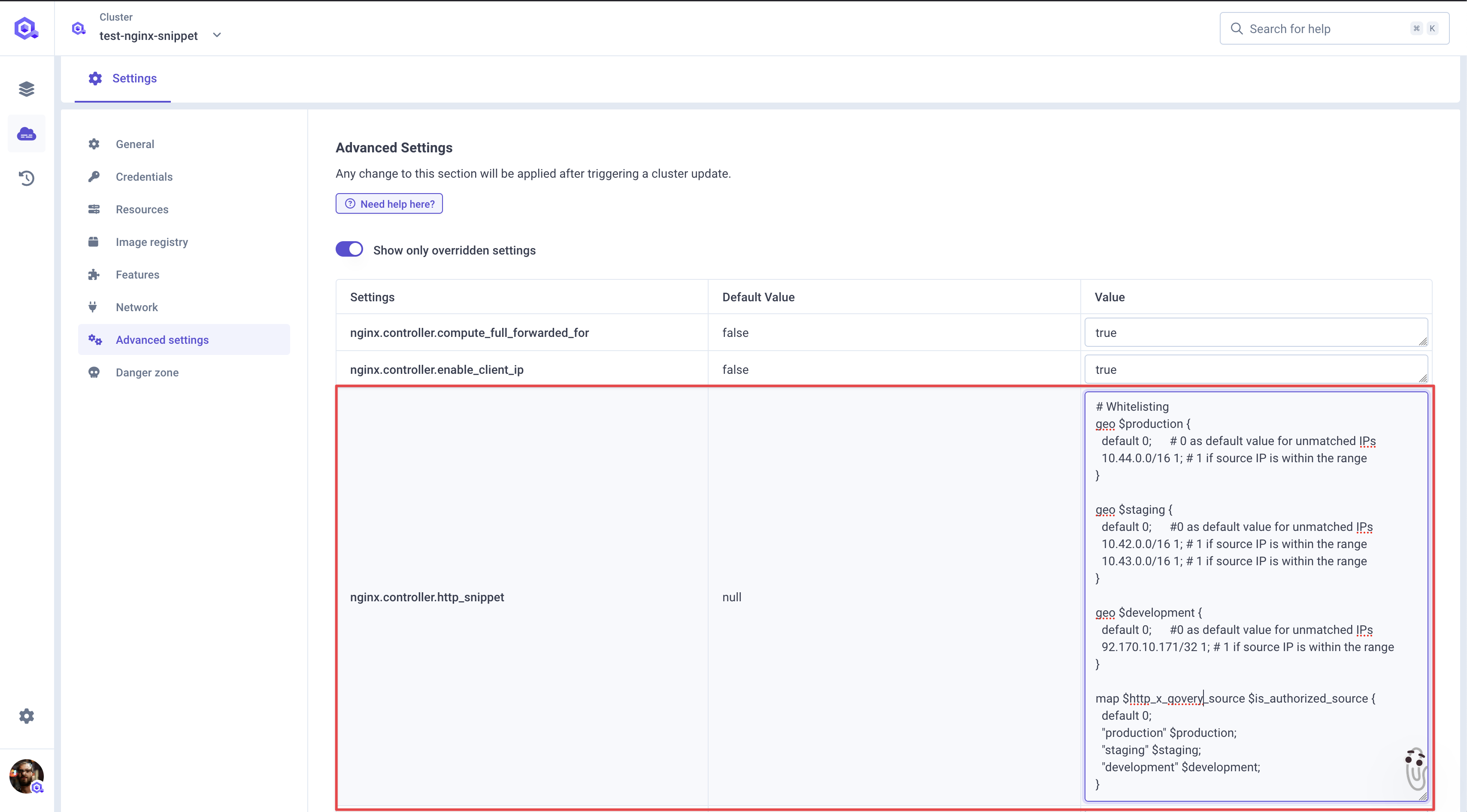
- The
geodirective classifies clients by IP address - The
mapdirective correlates the header value with authorization status - Combined, they enforce both IP range validation and header presence requirements
Step 2: Server Snippet Configuration
Configurenginx.controller.server_snippet:
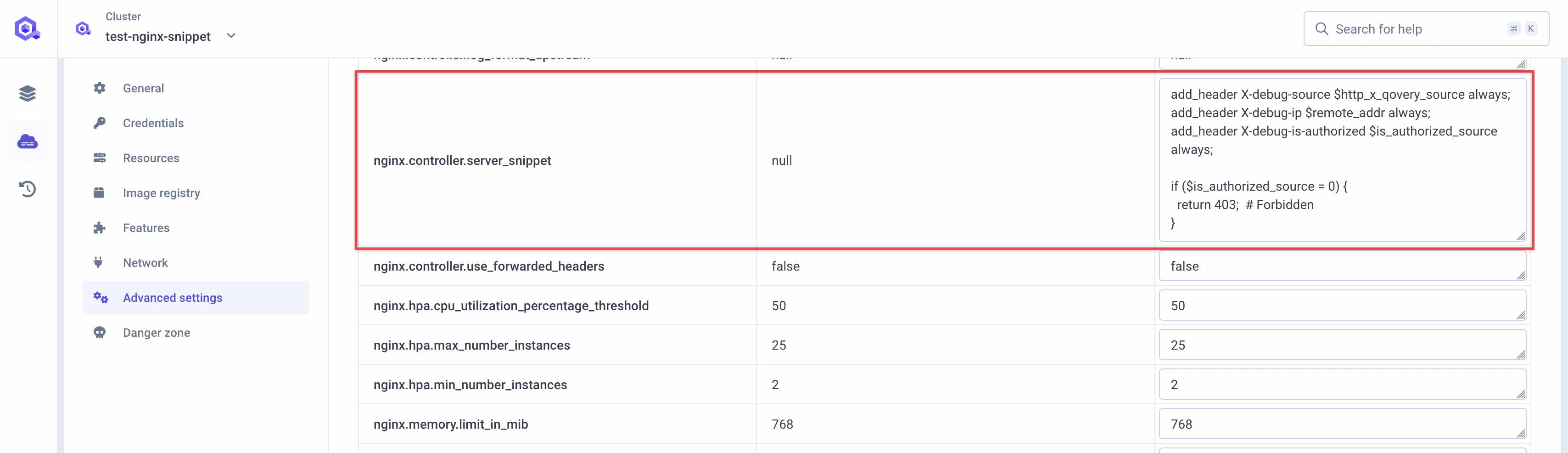
X-debug-source: Value of theX-QOVERY-SOURCEheaderX-debug-ip: Client’s IP addressX-debug-is-authorized: Whether the request is authorized (0 or 1)
Step 3: Deploy Configuration
Deploy the cluster to apply the changes: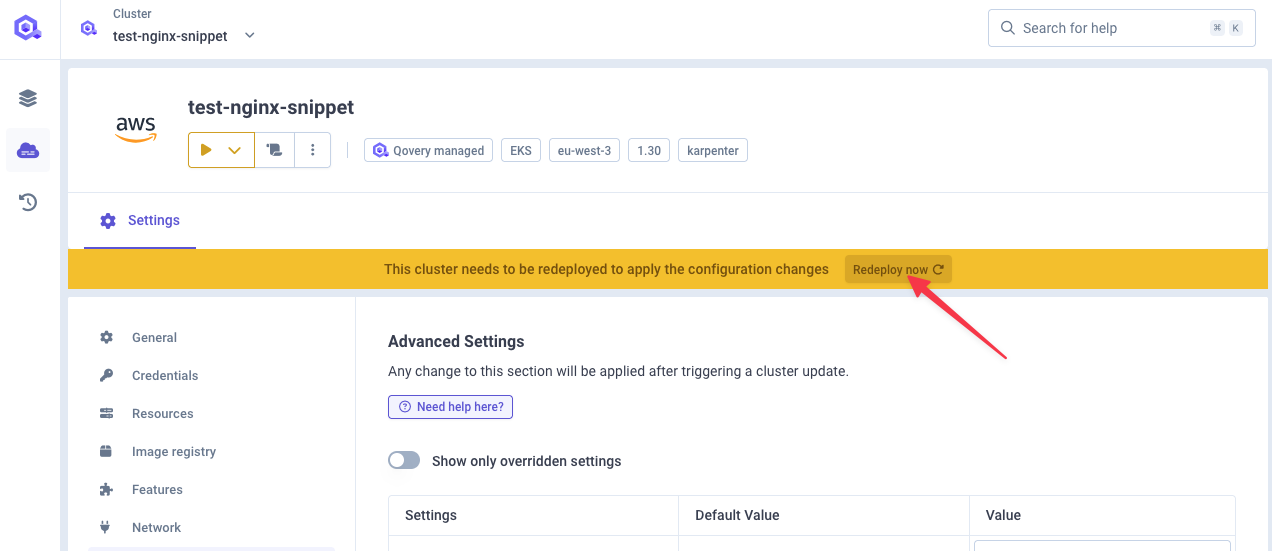
Testing Results
Test Case 1: No Header, IP Outside Range
Request:x-debug-source:(empty)x-debug-is-authorized: 0
Test Case 2: Production Header, IP Outside Range
Request:
Test Case 3: Development Header, IP Inside Range
Request:x-debug-source: developmentx-debug-is-authorized: 1
Advanced Scenarios
Multiple Headers
You can extend the configuration to support multiple headers:Time-Based Access
Combine with NGINX time variables:Rate Limiting per Source
Combine with rate limiting:Troubleshooting
All requests return 403
All requests return 403
- Check debug headers to see actual values
- Verify IP ranges match your environment
- Ensure header name matches exactly (case-sensitive)
- Check NGINX logs for syntax errors
IP not detected correctly
IP not detected correctly
- Verify
enable_client_ipis enabled - Verify
compute_full_forwarded_foris enabled - Check if you’re behind a load balancer or CDN
- Review
X-Forwarded-Forheader values
Configuration not applying
Configuration not applying
- Ensure cluster was deployed after changes
- Check cluster logs for NGINX configuration errors
- Verify no syntax errors in NGINX snippets
- Test NGINX configuration:
nginx -t
Security Considerations
Header spoofing
Header spoofing
Custom headers can be spoofed by clients. Always combine header validation with IP whitelisting for security-critical applications.
IP address changes
IP address changes
If clients use dynamic IPs, consider:
- Using broader IP ranges
- Implementing token-based authentication instead
- Using VPN connections with static exit IPs
Debug headers in production
Debug headers in production
Remove debug headers in production to avoid information disclosure:
Conclusion
The configuration demonstrates hownginx.controller.http_snippet and nginx.controller.server_snippet enable scalable, flexible access control rules combining IP restrictions and HTTP header validation for multi-tenant environments.

