Overview
Qovery handles most maintenance tasks automatically, including:- Kubernetes cluster updates
- Infrastructure component upgrades
- Security patches
- Cloud provider managed service updates
- Certificate renewals
- Load balancer updates
Kubernetes and Component Updates
Automatic Updates
Qovery handles Kubernetes patches and upgrades using your cloud provider’s native update mechanisms. This ensures compatibility across all infrastructure components:- Kubernetes Control Plane - Automatically upgraded to latest stable versions
- Nginx Ingress Controller - Updated to maintain compatibility with Kubernetes
- Cert-Manager - Certificate management component updates
- CNI (Container Network Interface) - Network plugin updates
- CSI (Container Storage Interface) - Storage plugin updates
- Karpenter - Auto-scaling component updates
Update Strategy
Qovery employs rolling update strategies to prevent downtime:- Security Patches - Applied automatically as soon as available
- Minor Updates - Deployed automatically after testing
- Major Kubernetes Updates - Applied by Qovery after thorough validation to ensure component compatibility
Rolling updates ensure your applications continue running while infrastructure is being updated. New nodes are added before old ones are drained.
Important Notes
Best Practice: Always deploy through Qovery to ensure proper maintenance and support.Managed Services
Database and Managed Services
By default, every managed service deployed by Qovery is configured with automatic patches and upgrades proposed by the cloud provider. What’s Automatic:- Security patches
- Minor version updates (e.g., PostgreSQL 14.1 → 14.2)
- Operating system patches
- Performance improvements
- Major version upgrades (e.g., PostgreSQL 14 → 15)
- Breaking changes that may require application updates
- Migration to new database engine versions
Maintenance Windows
Managed services typically perform automated updates during configured maintenance windows:- Default Window: Sunday 02:00-06:00 AM (your cluster timezone)
- Duration: Updates usually complete in minutes
- Impact: Minimal to zero downtime for most updates
- Go to your database service settings
- Configure maintenance preferences
- Choose a window that minimizes impact on your users
Cloud Provider Quotas
Understanding Quotas
Cloud providers impose limits on resources you can use:- Compute: Number of vCPUs, instances
- Storage: Volume size, IOPS, snapshots
- Networking: Load balancers, IP addresses, VPCs
- Services: Database instances, managed services
When You Hit Limits
When you encounter cloud provider limits, Qovery displays the information in infrastructure or application logs. Example Error Messages:Requesting Quota Increases
You must contact your cloud provider directly to request quota increases:- AWS
- GCP
- Azure
- Scaleway
- Go to AWS Service Quotas Console
- Select the service (e.g., EC2, VPC, RDS)
- Find the quota you need to increase
- Click Request quota increase
- Provide business justification
- Submit request
Most cloud providers are happy to increase quotas for legitimate production workloads. Be specific about your needs and expected growth.
Credential Rotation
For security compliance, rotating cloud credentials regularly is a best practice. Qovery supports both manual and automatic credential rotation.Manual Credential Rotation (Recommended)
The recommended approach creates a new access key, deploys it to Qovery, waits for completion, then deletes the old key—avoiding downtime during updates.Create New Access Key in AWS
- Go to AWS IAM Console
- Navigate to Users
- Select your Qovery IAM user
- Click Security credentials tab
- Scroll to Access keys section
- Click Create access key
- Save the new Access Key ID and Secret Access Key
Update Credentials in Qovery
- Log into Qovery Console
- Go to Organization Settings → Cloud Credentials
- Find your AWS credentials
- Click Edit
- Enter the new Access Key ID and Secret Access Key
- Click Save
Deploy Cluster with New Credentials
- Go to Clusters
- Select your cluster
- Click Update (or wait for next deployment)
- Monitor the deployment logs
- Wait for deployment to complete successfully
The cluster will reconnect using the new credentials. This process takes 5-10 minutes.
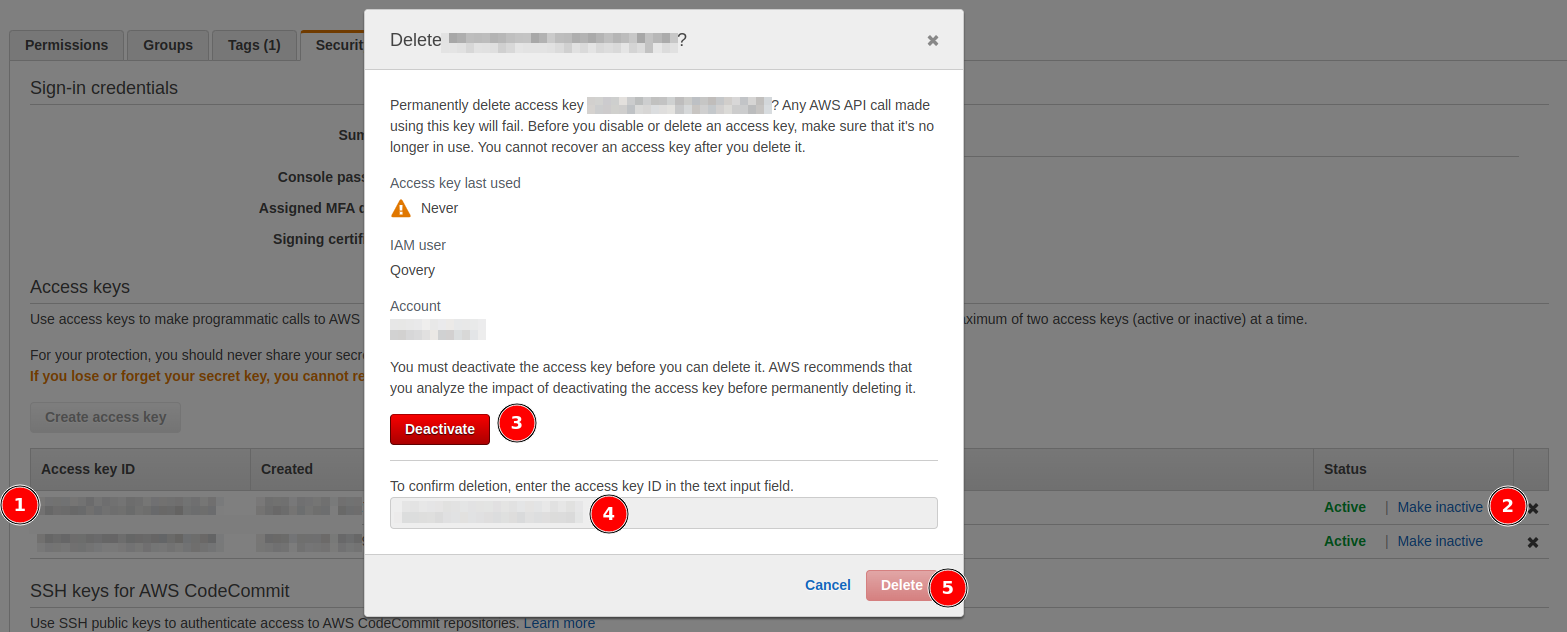
Delete Old Access Key
- Return to AWS IAM Console
- Navigate to your Qovery IAM user
- Go to Security credentials tab
- Find the old access key (check creation date)
- Click Delete
Automated Credential Rotation (Advanced)
You can automate credential rotation using the Qovery API and cloud provider CLIs. Requirements:- Qovery API token
- AWS CLI configured
jqfor JSON parsing- Bash environment
- Save as
rotate-credentials.sh - Update configuration variables
- Make executable:
chmod +x rotate-credentials.sh - Run:
./rotate-credentials.sh
Maintenance Best Practices
Schedule regular maintenance reviews
Schedule regular maintenance reviews
- Review cluster health monthly
- Check for available Kubernetes updates
- Monitor resource quotas and plan increases
- Audit IAM credentials and rotate every 90 days
Monitor maintenance notifications
Monitor maintenance notifications
- Check Qovery status page regularly
- Subscribe to cloud provider maintenance notifications
- Review deployment logs after automatic updates
- Test applications after major updates
Plan for major upgrades
Plan for major upgrades
- Test major database version upgrades in staging first
- Schedule upgrades during low-traffic periods
- Have rollback plans ready
- Communicate maintenance windows to users
Keep documentation updated
Keep documentation updated
- Document custom configurations
- Maintain runbooks for common issues
- Track infrastructure changes
- Share knowledge with your team
Maintenance Windows and Downtime
Zero-Downtime Updates
Most Qovery maintenance operations are performed with zero downtime:- Kubernetes node updates - Rolling updates with pod migration
- Load balancer updates - Blue-green deployments
- Certificate renewals - Automatic with no interruption
- Infrastructure patches - Applied to standby nodes first
Planned Maintenance
For rare cases requiring downtime:- Advance Notice: Qovery notifies you at least 7 days before
- Maintenance Window: Typically 1-4 hours
- Status Updates: Real-time updates via status page
- Post-Maintenance: Verification and health checks

