
Ephemeral Environments for Full-Stack (Backend + Frontend)



Ephemeral environments dominate conversations, but most teams focus only on the frontend—missing half the story. Without backend services, databases (DBs), and message queues, teams can’t validate real-world scenarios. Frontend previews lack API interactions, transactional data flows, and event-driven architectures—critical for testing microservices, real-time data pipelines, or third-party integrations.
Backend ephemeral environments are a different beast—stateful, interdependent, and data-heavy. Let’s discuss why they’re essential and why most teams should buy, not build, them.
What Are Full-Stack (Backend + Frontend) Ephemeral Environments?
Definition: Full-stack ephemeral environments are disposable, on-demand replicas of your production stack, including:
- Frontend: Static apps (React, Vue), server-side rendered apps (Next.js, Nuxt), or mobile backends.
- Backend: APIs (REST/gRPC), microservices (Node.js, Python, Java), and serverless functions.
- Data Layer: Databases (PostgreSQL, MongoDB), message queues (RabbitMQ, Kafka), and caches (Redis).
- Infrastructure: Cloud resources (AWS/GCP/Azure), networking (VPCs, subnets), and secrets (API keys, tokens).
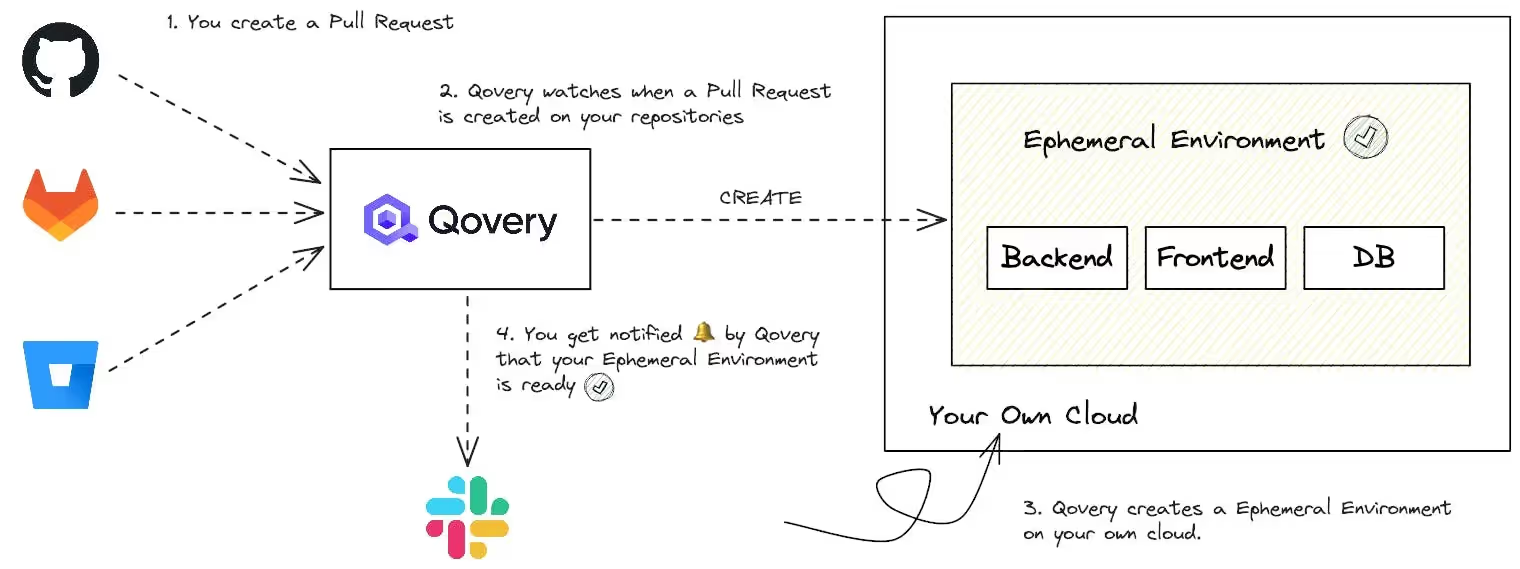
These environments are automatically created (e.g., on Git branch push or PR creation) and destroyed after use (e.g., PR merge or closure).
Now that we understand what a full stack ephemeral environment is, let’s go through some of the key use cases.
Use Cases
- Feature Previews:
Allow stakeholders to test a loan application process, insurance claim workflow, or patient record update end-to-end, including API calls to external verification services and real-time database updates. - QA Testing:
Run integration tests against isolated environments to validate payment processing flows (e.g., Stripe webhooks, order DB writes). - End-to-End Testing:
Simulate user journeys spanning frontend clicks, backend API calls, and DB transactions (e.g., Simulate complex user workflows across frontend, backend, and databases, such as financial transaction approvals, multi-step authentication flows, or data synchronization between SaaS platforms). - Integration Validation:
Test interactions between microservices (e.g., auth service ↔ billing service) without conflicting with other dev branches.
Expected Features
Isolated API + DB Per Branch/PR:
- API Isolation: Dedicated instances of backend services (e.g., Kubernetes pods per PR with unique namespace labels).
- DB Isolation: Branch-specific database clones using PostgreSQL’s pg_clone or cloud-native solutions (AWS RDS Clone).
- Queue Isolation: Temporary RabbitMQ vhosts or Kafka topic prefixes to prevent cross-environment message mixing.
Real Datasets:
- Snapshotting: Restore a production-like dataset using tools like pg_dump (PostgreSQL) or mongodump (MongoDB).
Example: Clone a 100GB production DB into a PR environment in 5 minutes using AWS RDS Snapshots. - Data Masking: Anonymize PII (e.g., replace real emails with user_[ID]@example.com) using tools like PostgreSQL’s pg_anonymize or custom regex scripts.
- Synthetic Data: Generate fake but structurally valid datasets (e.g., mock e-commerce orders with tools like Faker.js or Mockaroo).
Auto-Created and Auto-Destroyed:
- Network Isolation: Spin up environments in dedicated cloud VPCs or Kubernetes namespaces with strict ingress/egress rules (e.g., AWS Security Groups blocking cross-VPC traffic).
- Service Discovery: Automatically assign URLs (e.g., pr-23.env.yourcompany.com) using Traefik or Kubernetes Ingress controllers.
- Secure Secret Injection: Inject environment-specific secrets (e.g., Stripe test API keys) via HashiCorp Vault or AWS Secrets Manager, scoped to each ephemeral environment.
Why It’s So Hard to Build Them Yourself (And Why Most Teams Struggle)
While ephemeral environments simplify testing and validation, implementing full-stack versions presents unique infrastructure challenges, below are some of those.
Backend Complexity
Stateful Components:
- Databases:
- Storage Challenges: Cloning large databases for every PR requires significant SSD storage, that may lead to substantial recurring costs per developer.
- Data Consistency: Ensuring snapshots are transactionally consistent (e.g., no partial writes during pg_basebackup). - Queues/Streams:
- Resetting Kafka consumer offsets to replay test events without duplicating messages.
- Isolating RabbitMQ queues to prevent test data from leaking into prod. - APIs: Managing version mismatches (e.g., PR #34 uses API v2.1, while PR #35 uses v2.2).
DB Cloning & Data Handling:
- Anonymization: Masking credit card numbers using regex (\d{4}-\d{4}-\d{4}-\d{4} → ****-****-****-1234) without breaking referential integrity.
- Synthetic Data Generation: Creating realistic test datasets for healthcare apps (e.g., HIPAA-compliant mock patient records via Synthea).
Secrets, Networking, and Private APIs:
- Secret Conflicts: PR #23 and PR #24 both needing a STRIPE_TEST_KEY, but with different values for isolated testing.
- Secure Credentials: Rotating short-lived AWS STS tokens per environment to avoid hardcoding secrets in CI/CD pipelines.
- Private API Access: Exposing internal gRPC services securely via TLS/mTLS in ephemeral environments.
Long Setup Time
- Infra-as-Code (IaC): Writing 500+ lines of Terraform/Pulumi code to provision AWS resources (EC2, RDS, S3) per environment.
- CI/CD Automation: Building GitHub Actions/GitLab CI pipelines to:
- Trigger environment creation on PR.
- Run integration tests.
- Tear down resources post-merge. - Clean-Up Automation: Preventing "orphaned" cloud resources (e.g., unclaimed EBS volumes) with AWS Lambda functions or Kubernetes CronJobs.
Ongoing Maintenance
- Fixing Broken Pipelines: Debugging why a Terraform apply failed during environment creation (e.g., AWS API rate limits, IAM permission errors).
- Infra/Cloud Updates:
- Migrating environments from Kubernetes 1.27 to 1.29 without breaking Istio sidecar injections.
- Upgrading PostgreSQL 13 → 14 across all ephemeral DB clones. - Scaling Challenges:
- Resource Contention: 50 parallel environments overloading a single Redis instance, causing timeouts.
- Cloud Spend Management: AWS bills spiking due to unoptimized EC2 instance types (e.g., using m5.xlarge instead of t3.medium for test environments). - Debugging Failures:
- Persistent Logging: Aggregating logs from short-lived environments using Fluentd or Datadog.
- Post-Teardown Analysis: Retaining traces for 7 days via Jaeger or AWS X-Ray to debug why a payment service failed in a destroyed environment.
Build vs. Buy: Which Approach Makes Sense?
Build Only If…
- You Have a Dedicated Platform/DevOps Team:
Requires 5–10 engineers skilled in IaC (Terraform, Crossplane), Kubernetes orchestration, and database tooling (e.g., PostgreSQL logical replication).
Example: A fintech company with legacy on-prem systems might need custom scripts to clone IBM Db2 databases. - Extreme Customization Demands:
Unique compliance requirements (e.g., air-gapped environments for govtech) or proprietary protocols (e.g., custom MQTT brokers). - Long-Term Maintenance Capacity:
Willing to allocate 20–30% of DevOps bandwidth indefinitely to fix pipeline failures, cloud compatibility issues, and scaling bottlenecks.
The Hidden Costs of Building
- Development Time:
6–12 months to build a stable system. Example: Writing a Kubernetes operator to automate namespace creation, Istio routing, and Argo CD syncs. - Ongoing Maintenance:
- Pipeline Debugging: Diagnosing why a DynamoDB clone failed (Was it IAM role permissions? A Terraform state lock?).
- Infra Upgrades: Migrating environments from Kubernetes 1.26 to 1.29 without breaking service discovery.
- Cost Leaks: Leftover cloud resources (orphaned disks, idle load balancers) burning $5k/month unnoticed. - Opportunity Cost: Engineers maintaining environments aren’t building product features.
Why Buying Accelerates Teams
- Instant Integration: Solutions like Qovery plug into GitHub/GitLab, auto-creating environments per PR with backend, DB, and queues.
- Zero Maintenance: Vendors handle security patches (e.g., Log4j vulnerabilities), cloud provider API changes (AWS SDK updates), and scaling.
- Cost Predictability: Pay-per-environment pricing vs. unpredictable cloud bills (e.g., $1.50/hour per full-stack environment).
Build vs. Buy Summary Table

What to Look for in a Solution (Key Criteria)
Full-Stack Support
Must-Have:
- Backend services (REST/gRPC APIs, WebSocket servers).
- Databases (SQL/NoSQL), caches (Redis), queues (Kafka, SQS).
- Service mesh compatibility (Istio, Linkerd) for advanced routing.
Red Flag: Solutions that only handle frontend containers.
Database Cloning & Data Management
Critical Features:
- Instant Cloning: Cloud-native DB branching (e.g., Neon’s instant Postgres clones, PlanetScale’s Vitess branching).
- Data Masking: Automated PII anonymization (e.g., GDPR-compliant email/phone masking).
- Test Data: Synthetic data generators (e.g., Mockaroo for CSV, Synthea for healthcare).
Avoid: Tools that require manual SQL dumps or full DB copies (slow, storage-heavy).
Secrets and Configuration
Non-Negotiable:
- Dynamic Secrets: Inject environment-specific API keys (e.g., Stripe test keys) via Vault or AWS Secrets Manager.
- Conflict Prevention: Isolate secrets per environment (dev/test staging can’t access prod keys).
- Audit Trails: Track secret access (SOC2 compliance).
CI/CD Integration
Key Integrations:
- GitHub Actions, GitLab CI, CircleCI.
- Auto-spin environments on PR creation, block merges if E2E tests fail.
Advanced: Custom webhooks to trigger environments from Jira or Slack.
Cost & Scaling Controls
Essential:
- Auto-Pause: Sleep environments after 1 hour of inactivity (cuts cloud costs 60%).
- Resource Caps: Limit CPU/RAM per environment to prevent AWS bill surprises.
- Concurrency Limits: Queue environments during peak demand to avoid cloud quota hits.
Observability
Must-Have:
- Centralized Logs: Aggregate logs from ephemeral services (e.g., Datadog, ELK).
- Post-Mortem Traces: Retain traces for 7 days after environment deletion.
- Health Checks: Automated alerts for failed DB clones or hung APIs.
Vendor Lock-In Mitigation
Ask: Does the solution use open standards (OCI containers, Terraform) or proprietary APIs?
Ideal: Exportable configurations (e.g., generate Terraform files for your environments).
Conclusion — You Want Full-Stack? Don’t Reinvent the Wheel
Full-stack ephemeral environments are no longer optional for teams shipping complex backend logic. But building them internally is a resource sinkhole—unless you’re a hyperscaler with infinite cloud credits and engineers.
Buying a solution like Qovery offloads the grunt work: database branching, secret management, and cloud orchestration. Your team keeps velocity high, costs predictable, and focuses razor-sharp on what matters: your product.
Qovery’s Ephemeral Environments automate full-stack previews with zero maintenance. Spin up isolated backend services, databases, and queues per PR—directly in your cloud. Learn more at qovery.com.

Suggested articles
.webp)



.svg)
.svg)
.svg)











