Zero-friction DevSecOps: get instant compliance and security in your PaaS pipeline



Key Points:
- Manual Security Kills Velocity: Traditional "gate-keeping" security creates friction through complex secrets management, configuration drift, and manual compliance audits.
- The PaaS Advantage: By embedding security into the platform (PaaS), enforcement becomes automatic, consistent, and invisible to the developer.
- Qovery’s Approach: Qovery automates infrastructure hardening, runtime secrets, and access control, allowing teams to be audit-ready without touching config files.
Shifting security left shouldn't feel like hitting a wall. While every DevOps team aims to embed security without slowing delivery, the reality is often a mess of manual gates, complex secrets management, and panic-induced compliance audits. Instead of building features, engineers get stuck configuring tooling.
It creates a critical friction point: you have to choose between speed and safety. But what if you didn’t?
This guide explores why manual security integration is failing developers and how unified platforms can automate enforcement, creating a "Zero-Friction" DevSecOps experience where compliance is invisible, and deployment is instant.
The Three Operational Burdens of Manual Security
DevOps teams implementing security manually face recurring challenges that consume time and create ongoing maintenance burden.
1. Secrets Management Toil
Applications need credentials: database passwords, API keys, encryption keys, service account tokens. Managing these secrets securely requires significant infrastructure and process overhead.
Teams typically deploy HashiCorp Vault or similar solutions, then configure authentication backends, secret engines, and access policies. Applications require sidecar or init containers to fetch secrets at runtime. Each new service requires policy updates to grant appropriate access.
Secret rotation adds another layer of complexity. Secrets should change regularly, but coordinating rotation across applications without downtime requires careful orchestration. Many teams defer rotation indefinitely because the operational cost exceeds perceived benefit.
Environment-specific secrets multiply the burden. Development, staging, and production each need separate credentials. Keeping these synchronized while maintaining isolation demands careful attention. Mistakes lead to production credentials leaking into development or applications failing because secrets weren't provisioned in new environments.
The result is significant engineering time spent on credential plumbing rather than application development.
2. Configuration Drift from a Security Perspective
Infrastructure configurations drift over time as manual changes accumulate. Sometimes normal processes don’t apply and changes are made directly to the infrastructure, which aren’t tracked in code.
From a security perspective, configuration drift creates serious exposure. Untracked modifications to networking configuration, secrets, or policies widen the attack surface silently, making it hard for security teams to manage.
Detecting drift requires continuous auditing that most teams lack resources to perform. Security scanners identify issues at point-in-time but often miss changes between scans. By the time quarterly audits discover problems, the insecure configurations have existed for a while and could have been abused by attackers.
Remediating drift creates its own challenges, as tightening permissions may break applications that depended on overly broad access. Teams struggle to enforce strict configurations when they might cause production incidents.
3. Manual Compliance Gate Integration
Regulated industries require evidence that security controls exist and function correctly. SOC 2, HIPAA, PCI-DSS, and similar frameworks demand extensive documentation of access controls, encryption, audit logging, and vulnerability management.
Integrating compliance checks into development pipelines typically means configuring multiple specialized tools. Vulnerability scanners are set up to check container images, while static analysis tools examine infrastructure code. Policy engines validate configurations against organizational standards, and each tool requires setup, maintenance, and integration with CI/CD systems.
Documentation needs then to be compiled from those scattered resources, integrating all tooling outputs into a centralized source of truth to validate compliance requirements. This is time-intensive work that distracts from other impactful work security teams can perform.
The PaaS Pipeline as the Security Control Plane
The alternative to manual security integration is building security into the platform itself. A unified PaaS becomes the control plane where security enforcement happens automatically, consistently, and invisibly.
1. Automated Enforcement
When security controls are embedded in the platform, they execute without engineer intervention. Every deployment passes through the same security checks, and every new environment is provisioned with the same hardened configurations.
This automation removes the inconsistency that manual processes introduce. Engineers don't forget to run security scans because the platform runs them automatically. Configurations don't drift because the platform continuously reconciles the actual state against the desired state.
2. Code-Driven Security Policy
Platform-level security expresses as code rather than manual configurations. Security policies are defined in version-controlled files, all changes go through review processes, and audit trails show who changed what and when.
This approach makes security reproducible and testable, as new environments inherit security configurations automatically, and policy changes apply across all environments consistently. Rolling back problematic changes is also automated, with consistent versioning across all operations.
How Qovery Automates Security
Qovery Secure is a compliance tool for DevOps that implements security across four technical layers, automating what teams otherwise need to configure manually.
1. Infrastructure Security
Qovery provisions cloud infrastructure using Terraform and OpenTofu with security best practices applied automatically. Networks are configured with appropriate isolations, security groups follow least-privilege principles, and user roles scope to minimum required permissions.
This infrastructure as code approach ensures every cluster is provisioned identically. No manual configuration means no opportunity for drift, while the generated Terraform remains accessible for teams that need to audit or customize configurations.
2. Application Runtime Security
Secrets management integrates directly into the platform. Teams define environment variables through the Qovery interface, and the platform injects them securely at runtime without exposing values in logs, manifests, or version control.
External secret managers integrate through the platform and are configured automatically. The complexity of secret retrieval abstracts away from application code and deployment configurations.
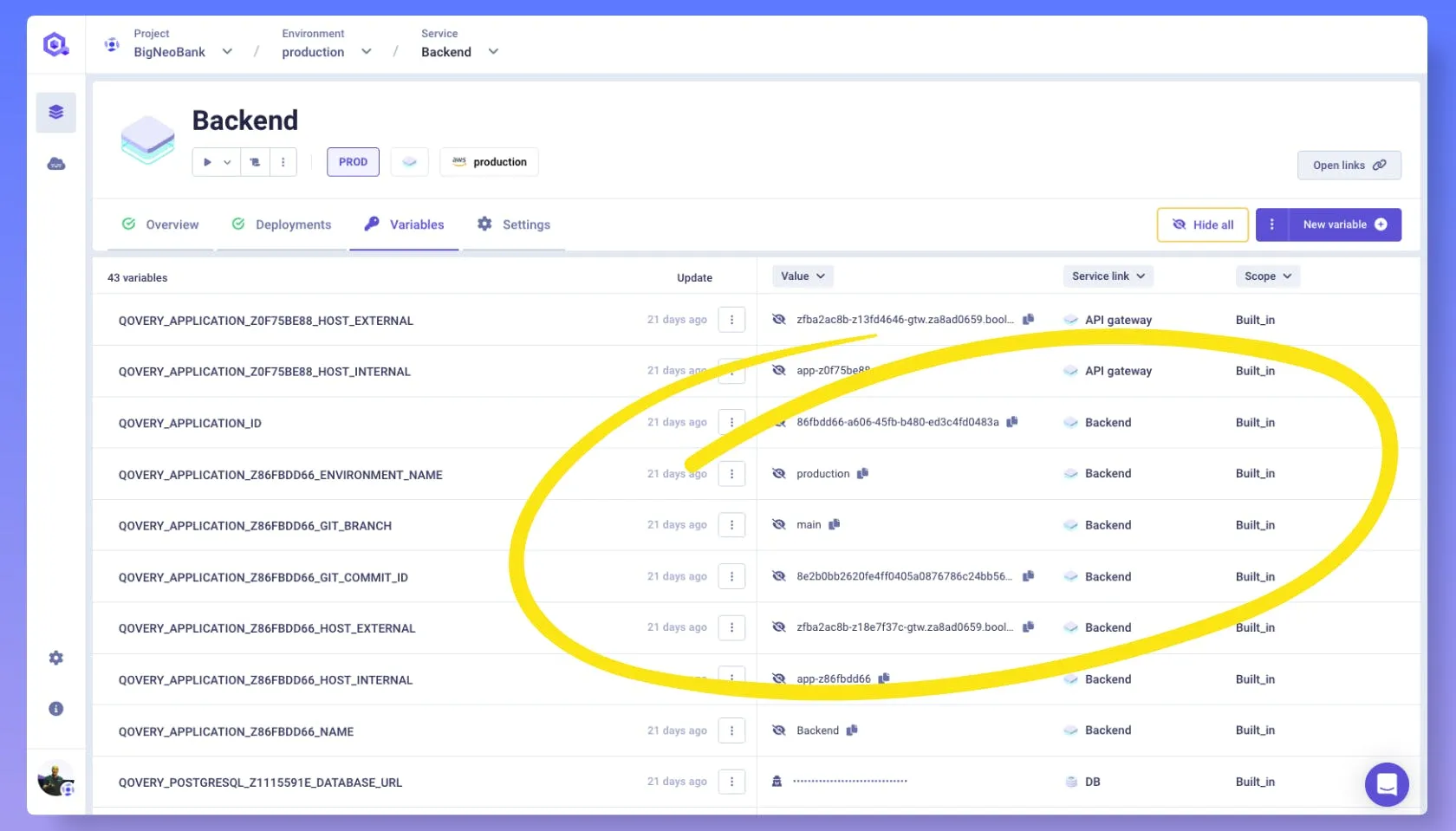
3. Access Control and Zero-Trust Architecture
Qovery implements a GitOps architecture that removes direct cluster access from the deployment path. In a normal environment, engineers don’t need direct cluster access as their deployment is automated and visible through the platform.
As deployments trigger through Git commits, the cluster can then reconcile its state by pulling and deploying new versions. Qovery holds cluster credentials internally, never exposing them to external systems, which reduces the attack surface compared to traditional CI/CD pipelines with broad deployment permissions.
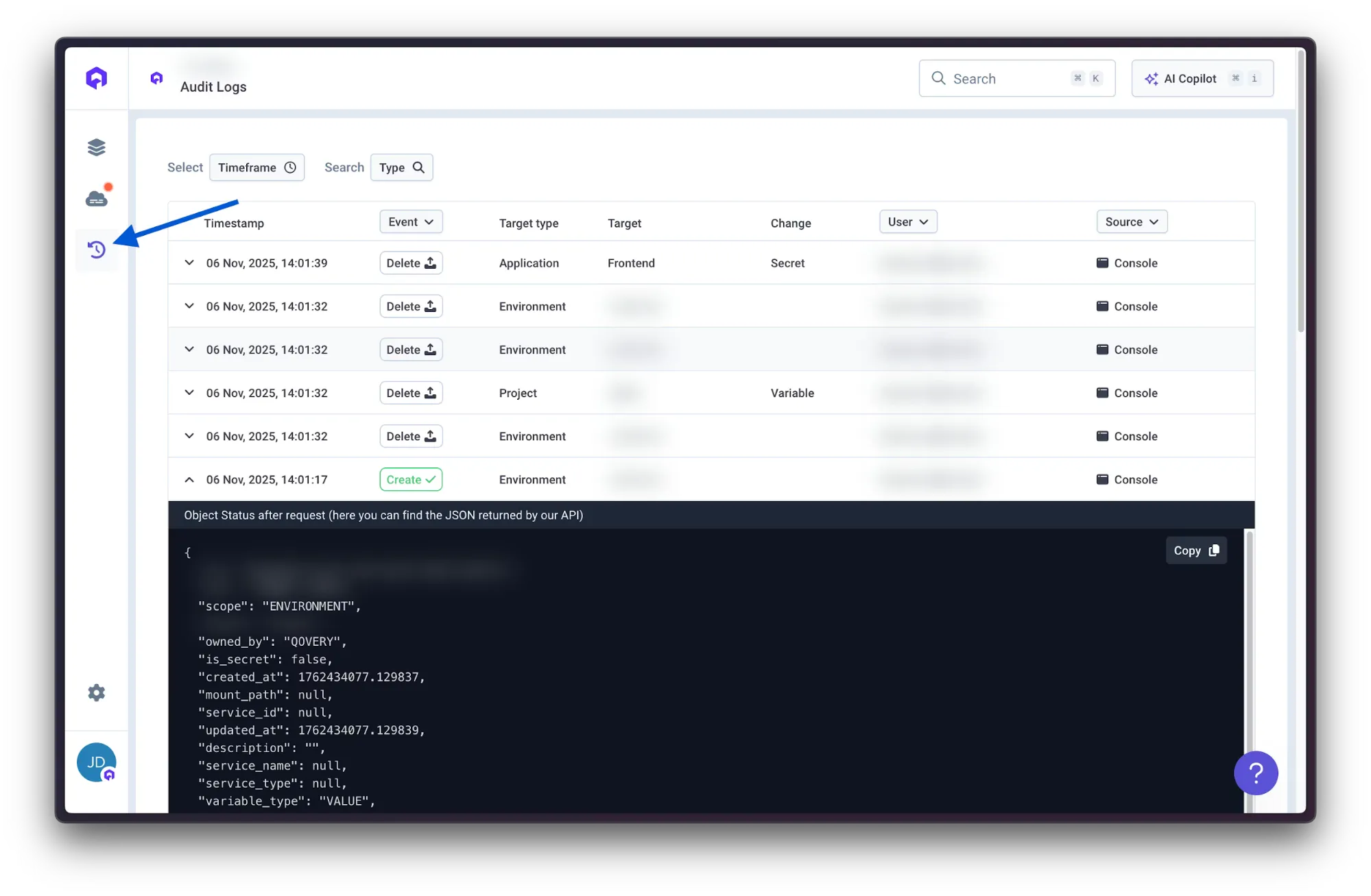
Role-based access control within Qovery governs who can modify environments, trigger deployments, or access logs. Permissions scope to specific projects and environments, and audit logs track all actions for compliance evidence.
4. Governance and Policy Enforcement
Qovery Secure enables organizations to codify security policies that enforce across all deployments. Environment restrictions prevent deploying untested code to production. Resource limits prevent configurations that could impact stability or cost.
These guardrails apply consistently without relying on engineer memory or discipline. Policy violations block at the platform level rather than discovered later in audits. Teams move fast within defined boundaries, confident that the platform prevents configurations that violate organizational standards.
Compliance as Code: Making Security Invisible
The goal of platform-level security is making compliance invisible to developers while remaining fully documented for auditors.
1. Developer Experience Without Friction
Developers interact with an automated platform through Git pushes and a web interface. Security happens in the background, as secrets inject automatically, scans run without manual triggering, and policies enforce without blocking workflows except when violations occur.
This experience is an improvement from manual security gates. Developers don't wait for security team approval on routine deployments, and they don't configure security tooling or maintain scanner integrations. They focus on application code while the platform handles security.
2. Platform Team Focus on Strategy
DevOps and platform engineers shift from configuring security tooling to defining security policy. The automated platform takes this strategy and handles implementation and maintenance for the engineering organization.
This shift elevates platform team contribution from operational maintenance to strategic governance. Time previously spent on secrets rotation, scanner updates, and compliance documentation redirects toward improving developer experience and platform capabilities. This strategy continuously improves the security posture while delivering a better environment for engineering teams to work in.
3. Audit-Ready Documentation
Compliance evidence is generated automatically from platform operation, continuously and without fail. Access logs, deployment history, configuration state, and policy enforcement are all recorded in formats suitable for auditor review.
When any compliance requirement demands evidence of access controls, the platform can provide it directly. Security assessments are met with automatic vulnerability scans, for which the results are historically maintained. The documentation burden that manual processes impose disappears as engineering organizations rely on proven platforms.
Conclusion
DevSecOps should not mean adding security responsibilities to already-stretched engineering teams. The modern approach embeds security into the platform itself, automating enforcement while eliminating operational burden.
Manual security integration creates friction through secrets management complexity, configuration drift, and compliance tooling maintenance. Each manual process requires ongoing attention that diverts engineers from higher-value work.
Unified platforms like Qovery automate security across infrastructure provisioning, application runtime, access control, and governance. Developers experience zero friction from security controls while platform teams focus on policy rather than implementation. Auditors also receive documentation automatically from the platform.
The result is velocity without compromise: fast deployments that remain secure, compliant environments that don't slow delivery, and engineering teams focused on building rather than configuring security tooling.

Suggested articles
.webp)



.svg)
.svg)
.svg)