Why Image Mirroring?
Image mirroring serves two main purposes:- Speed up deployments: By caching built images, Qovery avoids rebuilding identical images, significantly accelerating the deployment process
- Secure scale-up operations: When Kubernetes needs to scale up your application and create additional instances, having images stored locally ensures the operation succeeds even if the third-party registry is unavailable
How It Works
The mirroring registry is accessible and configurable through the Qovery interface under the “Mirroring registry” section of your cluster.For Applications Built by Qovery CI
When Qovery builds your application from Git: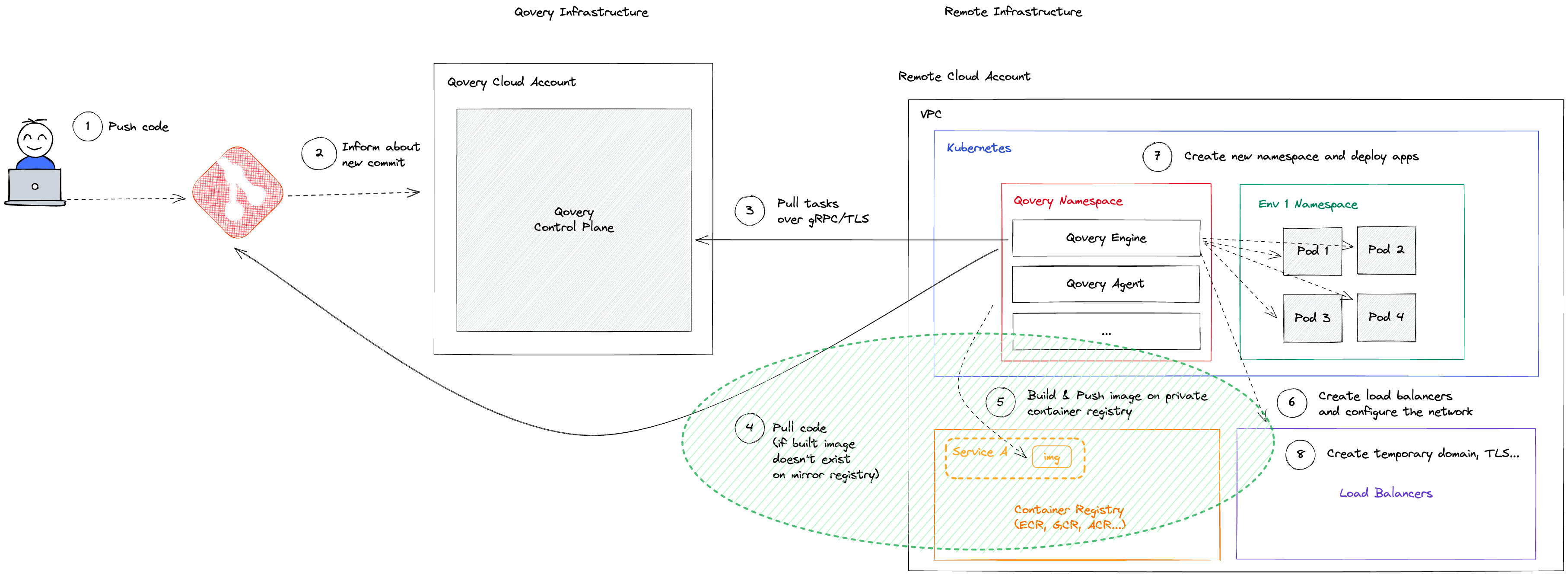
- After building, Qovery CI pushes the generated image to the mirroring registry
- Images are organized by Git repository with naming:
z<short_cluster_id>-git_repo_name - Image tags are derived from: commit ID, repository path, Dockerfile path, content, and ARGS variables
- Before building, Qovery checks if a matching image already exists
- If found, the build is skipped and the cached image is used
- Unused images are automatically deleted when no longer referenced
- Remote cache functionality (AWS, GCP, Scaleway) rebuilds only changed layers
For Applications from Third-Party Registries
The behavior depends on the configured mirroring mode:Service Mode (Default)
Each service maintains its own mirroring repository.
- Images are organized per Qovery service (isolated processes)
- Automatic cleanup when images become unnecessary
- Downside: Identical images across services are mirrored multiple times
Cluster Mode
All applications on the same cluster share one mirroring repository.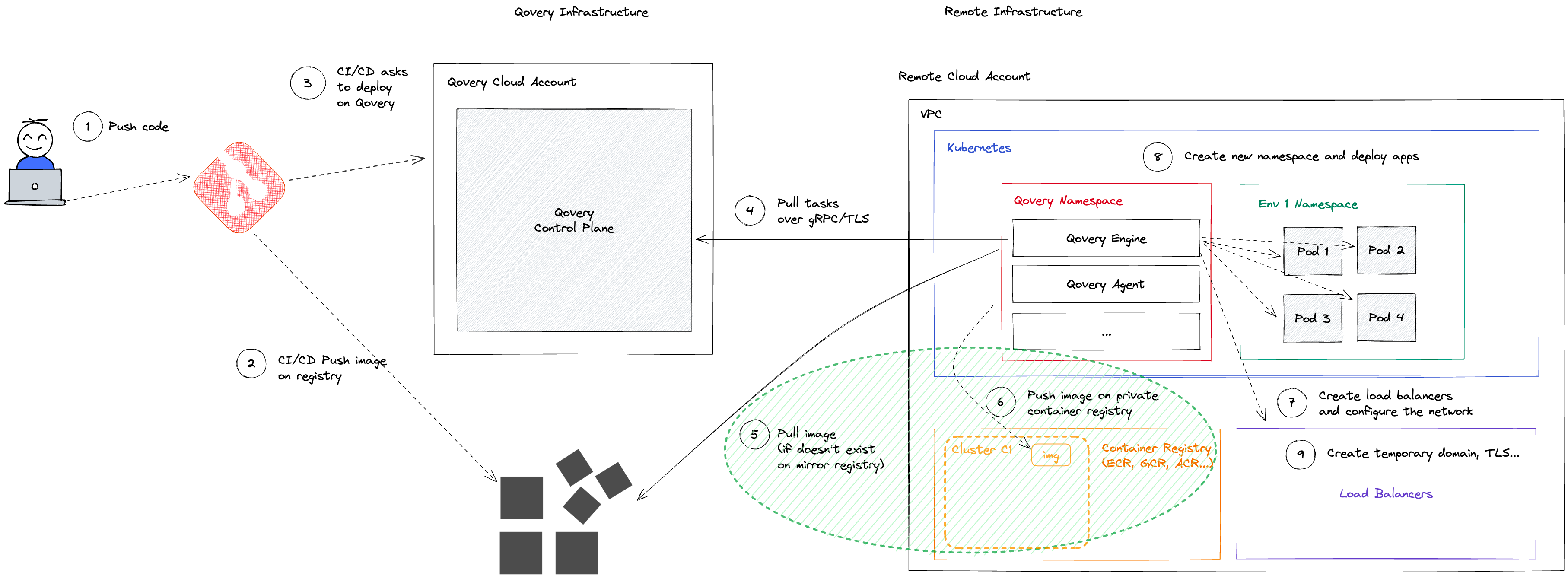
- Reduces duplication for shared images across environments
- Requires manual image management via TTL settings
- Not available on Scaleway
Important: Use Unique Image Tags
Using tags likelatest or other mutable tags can cause serious issues because the cached image in the mirroring registry may not be updated when you push a new version with the same tag.
Best practices:
- Use specific version tags:
myapp:v1.2.3,myapp:commit-abc123 - Use immutable digests:
myapp@sha256:abc123... - Avoid mutable tags like
latest,stable, orprod
Disabling Mirroring
To skip mirroring operations, you can push your built images directly into the mirroring registry within repositories that match your image names. Alternatively, if the source registry URL matches the cluster registry URL, mirroring is automatically skipped. Example for AWS: For an imagenginx with cluster registry https://32432542.dkr.ecr.eu-west-3.amazonaws.com:
Push to: https://32432542.dkr.ecr.eu-west-3.amazonaws.com/nginx
Image Retention Policy
Configurable TTL (Time To Live) settings control image retention duration via the advanced settingimage_retention_time.
Modifications to the retention policy only affect newly created repositories. Existing repositories remain unchanged.

