How To Manage Multiple Environments With Terraform in 2023



[Last updated on 07/26/2023]
Terraform Workspaces
One solution to this problem is to use Terraform Workspaces. Workspaces allow you to manage multiple environments within a single Terraform configuration. You can create a workspace for each environment and switch between them using the terraform workspace command. This allows you to maintain separate states for each environment and makes it easier to manage multiple environments within a single configuration.
While Terraform Workspaces can be a useful tool for managing multiple environments within a single configuration, there are some limitations to consider. For example, it can be challenging to navigate between environments, and it may be difficult to properly segregate backends and manage versioning between workspaces. In addition, Hashicorp themselves do not recommend using Workspaces as the sole solution for managing environments. According to Hashicorp,
"Workspaces alone are not a suitable tool for system decomposition because each subsystem should have its own separate configuration and backend, and will thus have its own distinct set of workspaces."
Terragrunt
Another solution is to use Terragrunt, which is a tool that can help simplify the process of managing multiple Terraform environments. It provides features such as environment segregation, variable file management, and remote backend segregation, which can make it easier to manage different environments within a single configuration. Terragrunt also makes it easier to manage versioning between environments compared to using Terraform Workspaces.
However, it is important to note that Terragrunt is a separate tool that operates differently from Terraform. This means that you will need to learn and understand how it works in addition to learning Terraform. While there is some code duplication involved in using Terragrunt, it is generally considered to be less complex than using branches (E.g, using different tfvars on different git branches) for managing environments.
For more information on using Terragrunt to manage multiple environments with Terraform, you may want to check out an article by Gruntwork that goes into greater detail on the topic.
Easier and scalable with Qovery
However, even with solutions like Terraform Workspaces and Terragrunt, managing multiple environments with Terraform can still be a complex and time-consuming task - especially with larger teams. This is where Qovery comes in.
Before we dive into the details of how Qovery can help here, let's take a look at the key challenges that Qovery aims to address:
- Ensuring proper segregation of environments
- Reusing code without duplication
- Providing self-service usage and control of environments
Environment and Services
In Qovery, we have a four-tiered structure for organizing applications: organization, project, environment, and service. Typically, our customers create one organization for their company and then create projects based on business cases. Within each project, they can create multiple environments, such as development, pre-production, and production. This allows for clear segregation of environments, making it easy to manage and deploy resources in the appropriate environment.
This structure is useful for organizing and segregating environments, but how does it help with managing code? That's a good question.
Environment Cloning
Environments are central to the functionality of Qovery. They are highly versatile units that can be cloned as often as needed, making them useful for creating templates. This provides several key benefits both from a coding and reusability perspective.
As an example, consider the process of creating an RDS instance. When writing code for an RDS instance, there are often a number of variables that need to be changed depending on the environment or scenario. For instance, a developer might want to test new application code with an RDS instance. In this case, they might choose to copy existing RDS instance code or use a module to spin up the desired instance. With Qovery, there is a simpler option: create an RDS service (inside your Environment) that references your code in your version control system (VCS) and import the necessary variables at the click of a button. This allows you to easily modify the template as needed and streamlines the process of spinning up an RDS instance.
This allows non-Terraform experts to spin up an RDS instance using Terraform code while changing the desired name and instance size through a UI.
The use of templates in Qovery allows you to reuse the same code across different environments, such as development, pre-production, and production, while simply changing a few key variables through a user interface or via code. You can also use the same code to spin up multiple instances in a single environment, such as development. One of the key benefits of this approach is that any changes made to the template code can be automatically applied to all environments using the template.
Furthermore, the power of Environments is not limited to small objects like RDS instances. Environments can be used to spin up entire VPCs or even full infrastructure stacks, providing a powerful and flexible way to manage your infrastructure.
Environment Variables and Secrets
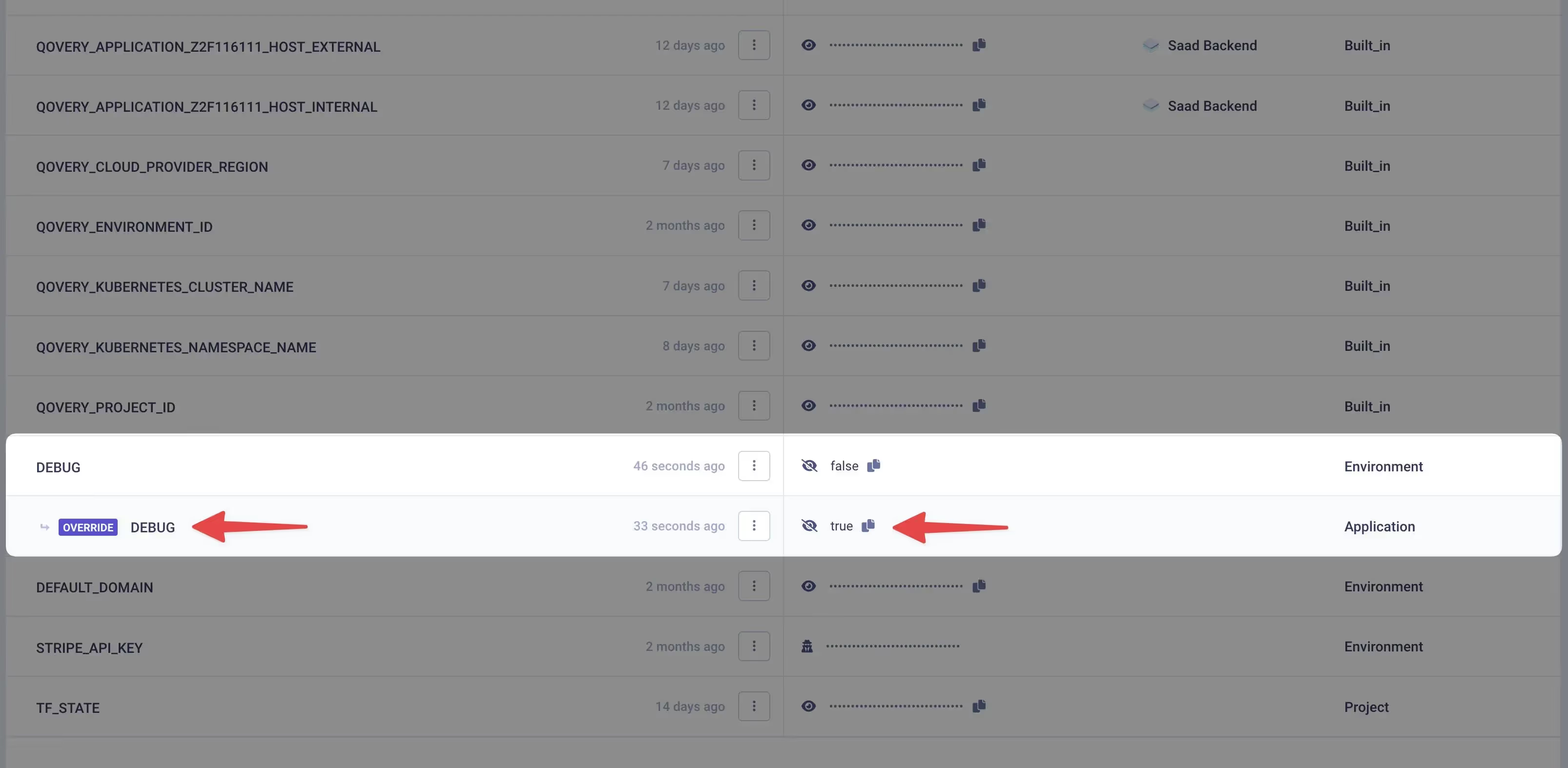
Qovery's Environments offer many powerful features beyond the ability to import and edit environment variables and secrets. With Qovery, you can define environment variables and secrets at any level of the application structure, from the organization level down to the service level. This allows you to specify environment variables and secrets, such as the region in which resources should be deployed within the environment. You can also override the value of certain environment variables and secrets for specific environments, for instance, to prevent the use of production environment variables in testing environments. Additionally, you can mark sensitive environment variables and secrets to ensure they are protected. For example, you might mark a project token as a sensitive environment variable or secret to ensure that it is not exposed to unauthorized users.
When using an Environment, you can easily see which environment variables and secrets have been inherited from the Environment and which have been inherited from the project. This helps you understand the values that are being used during the Environment run and can be useful for debugging and troubleshooting purposes.
Versioning
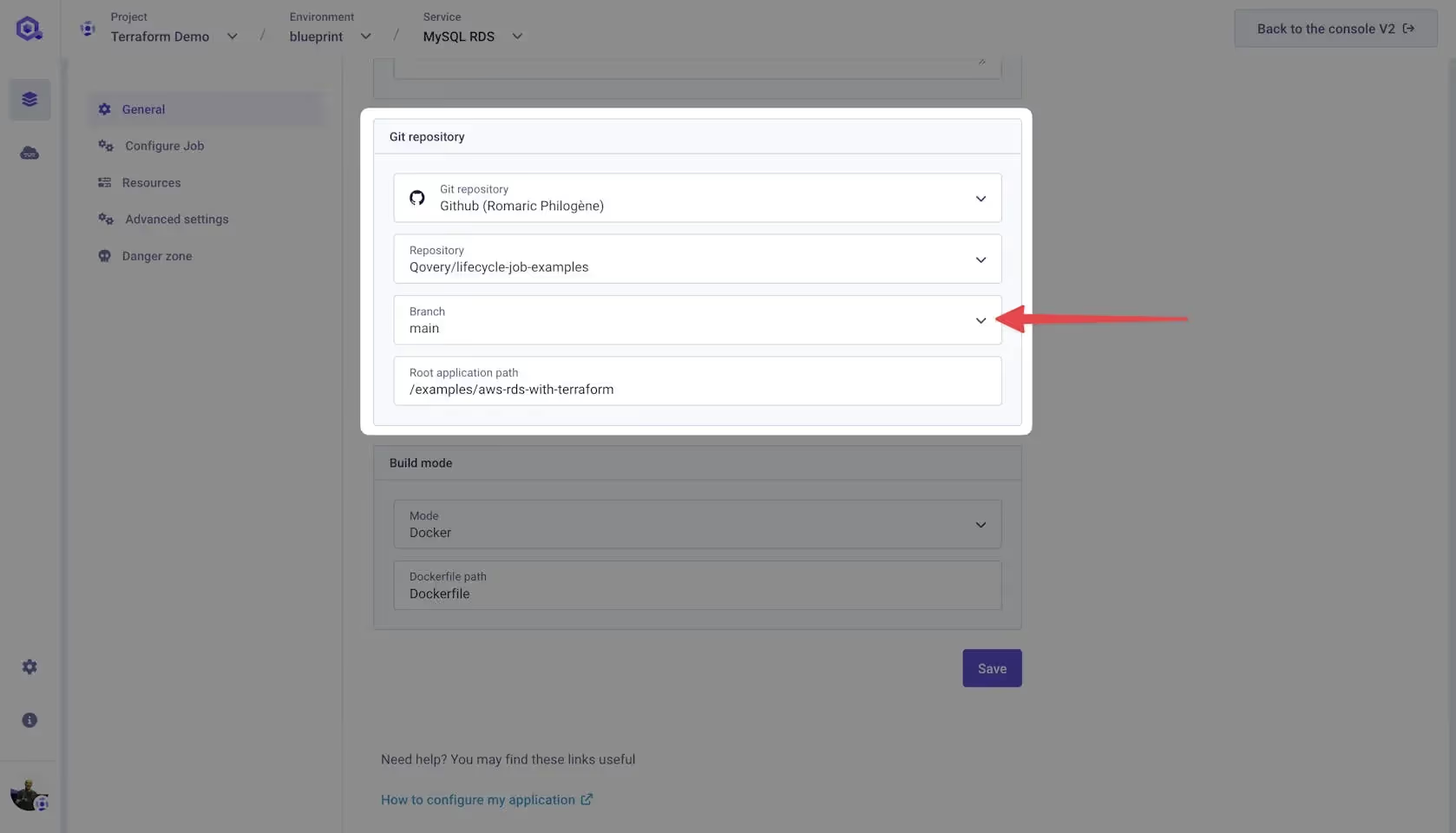
You might wonder how Qovery handles different versions or branches of the same code. Don't worry; we have you covered. With Qovery, you can specify which branch or tag of your code a service should use. This allows you to easily deploy different versions or branches of your code as needed without managing multiple copies of your code or configuration. Choose the branch you want to use, and Qovery will take care of the rest.
But you can also select the commit that you want to deploy.
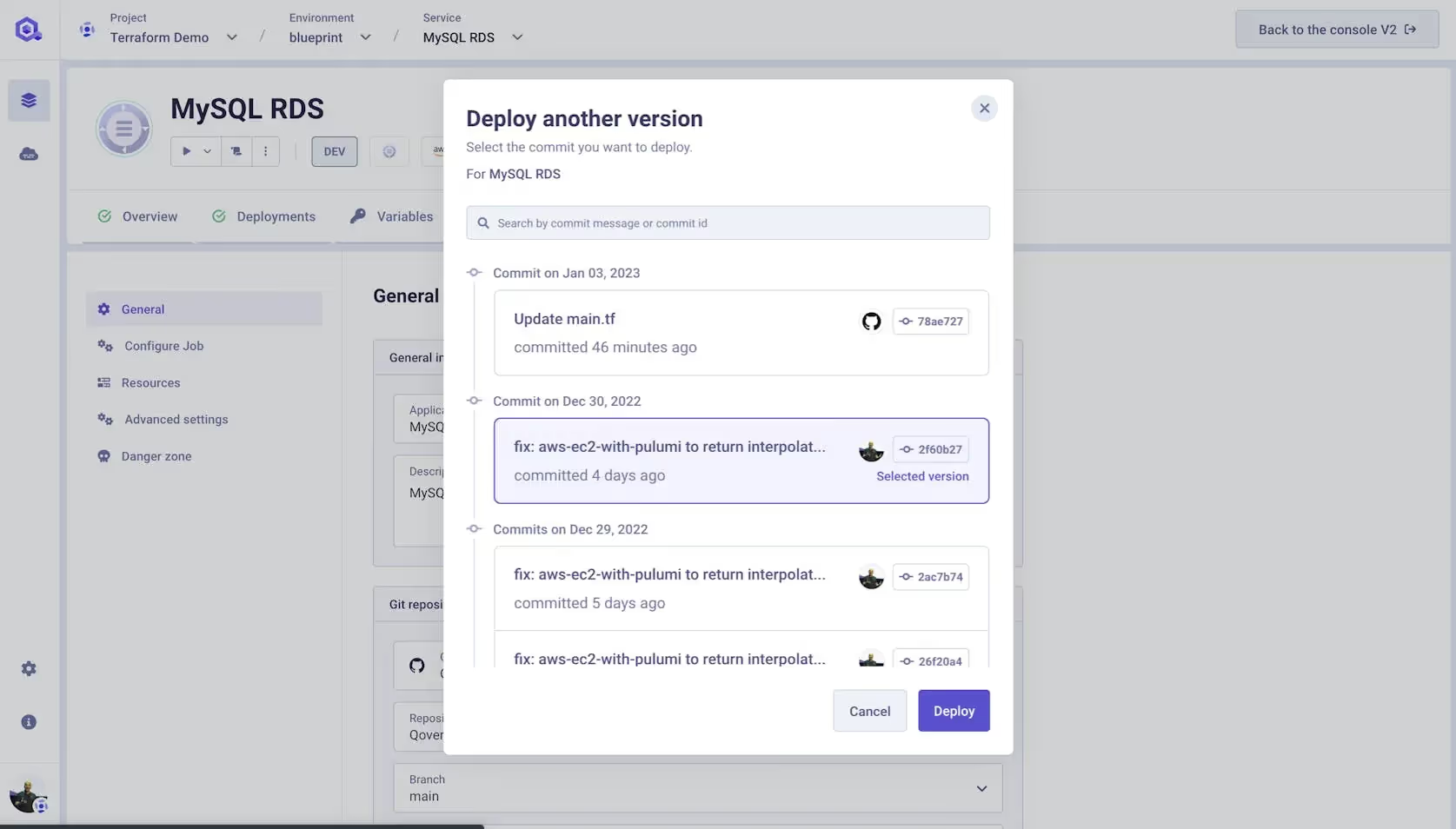
Impressed? Keep reading; it's getting even better.
Preview Environments
If you're a DevOps engineer working with Terraform, you know how important it is to preview and test changes before they go live. That's where Preview Environments come in! With Qovery, a new Preview Environment is automatically created whenever you open a Pull Request. This allows you to test and validate all the changes on a complete infrastructure before they go live. This can help you catch any issues before they become a problem and ensure that your code works as intended.
When the Pull Request is closed or merged, the Preview Environment is automatically destroyed, and all resources are torn down. This helps ensure that your work is secure and that you are only using resources when needed.
In short, Preview Environments are a super helpful tool for testing and validating changes before they go live.
Collaborative
As a DevOps engineer, it's crucial to collaborate with other teams, especially engineering teams, while still maintaining control over your work. With Qovery, you can quickly provide access to your environments and infrastructure to other teams while still retaining control over what they can see and do. This allows you to work more efficiently and effectively with other teams while still ensuring that your work is protected and secure. Whether you need to share access to a specific environment or grant access to an entire infrastructure stack, Qovery makes it easy to provide the necessary access while maintaining control.
Best Practices for Environment Isolation
- Separate State Files: Maintain separate state files for each environment to prevent cross-environment interference and unintended changes.
- Distinct Backend Configuration: Utilize different backend configurations, such as S3 buckets for AWS, segregated by access policies to ensure that state data is not accessible across environments.
- Variable Segmentation: Define environment-specific variables and use .tfvars files to manage distinct environment configurations securely.
- Access Control: Implement strict IAM policies or access roles that restrict who can perform actions in each environment, enforcing the principle of least privilege.
- Network Segregation: Employ separate VPCs or network spaces for development, staging, and production environments to eliminate the risk of cross-environment traffic.
- Resource Tagging: Tag resources with environment names and types to clearly identify them, enabling easier filtering and management, particularly during cost allocation and auditing.
- Automation Safeguards: Introduce automation safeguards like confirmation steps before critical actions are applied to production environments, reducing the risk of human error.
- Immutable Infrastructure: Aim for immutable infrastructure practices where changes are made by replacing resources rather than altering existing ones, thereby reducing drift between environments.
Integrations with CI/CD Pipelines
Incorporating Terraform and Qovery into CI/CD pipelines optimizes the release process by automating environment setup and application deployment. By using Qovery within CI/CD workflows, teams can:
- Automate Infrastructure Updates: Automatically trigger Terraform runs on code commits, ensuring that infrastructure changes are synchronized with application updates.
- Enforce Code Review: Require pull requests and code reviews for any Terraform changes, integrating with tools like GitHub Actions or GitLab CI to run plan and apply stages.
- Use Dynamic Environments: Leverage Qovery’s Preview Environments in the CI/CD pipeline to dynamically create and dispose of environments for testing features or hotfixes.
- Parallel Execution: Run multiple jobs in parallel to test and deploy to different environments, shortening the feedback loop and increasing development speed.
- Integration Testing: Facilitate comprehensive integration testing by provisioning temporary environments that mimic production, providing confidence in the deployment process.
- Security Scans: Integrate automated security scanning of Terraform code within the pipeline to detect misconfigurations or compliance issues before they are deployed.
- Rollback Strategies: Implement automated rollback capabilities within the pipeline in case of deployment failures, ensuring quick recovery of stable state.
Containerization and Kubernetes
Utilizing Terraform and Qovery for containerization and Kubernetes offers a robust method to handle application deployment across environments:
- Container Orchestration: Define Kubernetes resources with Terraform to orchestrate container deployment, scaling, and management systematically.
- Service Discovery: Use Qovery’s integration capabilities to manage service discovery within Kubernetes, ensuring smooth communication between microservices.
- Helm Charts: Manage Helm chart releases with Terraform, allowing for packaged application deployment across different Kubernetes clusters.
- Kubernetes Namespaces: Utilize Kubernetes namespaces to segregate resources within the same cluster, aligning with different environments managed by Qovery.
- Continuous Deployment: Set up continuous deployment to Kubernetes using Qovery, which automatically handles the container build and deployment process upon git push.
- Load Balancing and Ingress: Configure load balancers and ingress controllers using Terraform to control external access to applications, enabling secure and scalable public-facing services.
- Resource Limits: Define resource requests and limits for each container to ensure optimal resource utilization and prevent one environment from consuming all available cluster resources.
- Volume Management: Manage persistent volumes with Terraform to ensure stateful applications have consistent and reliable storage across container restarts and deployments
Conclusion
Managing multiple environments with Terraform can be tricky, but Query makes it easy! With our Preview Environments, you can test and validate changes before they go live, ensuring that your code works as intended. Our four-tiered application structure helps you reuse code and manage dependencies while maintaining control. In short, Qovery is one of the best solutions for managing multiple environments with Terraform.
What's next?
We would love to hear your thoughts on the approaches mentioned here or how you manage your Terraform environments. Feel free to share your experiences and insights with us.

Suggested articles
.webp)



.svg)
.svg)
.svg)